PETER HAYES
JANUARY 18, 2018
I. INTRODUCTION
In this essay, Peter Hayes concludes that: “Each nuclear armed state will make its moves in response to the posited terrorist nuclear attack partly in response to its expectations as to how other nuclear armed states will perceive and respond to these moves—and considered together, it is obvious that they may not share a common image of the other states’ motivations and actions in this response, leading to cumulative potential for misinterpretation and rapid subsequent action, reaction, and escalation.”
Acknowledgment: This report was funded by MacArthur Foundation. The author thanks John Carlson, Martha Crenshaw, Terrence Roehrig, Lee Sigal, and Ramesh Thakur for their review comments. The author alone is responsible for this text.
Peter Hayes is Director of the Nautilus Institute and Honorary Professor at the Centre for International Security Studies at the University of Sydney.
Paper prepared for Workshop Reducing Risk of Nuclear Terrorism and Spent Fuel Vulnerability in East Asia co-sponsored by Nautilus Institute and Research Center for the Abolition of Nuclear Weapons, Nagasaki University, Nagasaki, January 20-22, 2017
The views expressed in this report do not necessarily reflect the official policy or position of the Nautilus Institute. Readers should note that Nautilus seeks a diversity of views and opinions on significant topics in order to identify common ground.
Banner image: Nine sandcastles with beach-ball by from Pixabay.
II. NAPSNET SPECIAL REPORT BY PETER HAYES
NON-STATE TERRORISM AND INADVERTENT NUCLEAR WAR
JANUARY 18, 2018
Introduction
This paper has eight sections. The first revisits an old concept, that of catalytic nuclear attack in which a weak nuclear weapons state induces nuclear war between stronger nuclear weapons states seeking relative political and military advantage. The second part explores whether catalytic nuclear war, specifically induced by nuclear terrorism, is a serious policy concern in current conditions. The third section examines post-Cold War trends in non-state nuclear terrorism, and describes the different motivations, capacities, and goals that might drive such attacks. The fourth section reviews the actual record of non-state nuclear threats and attacks and concludes that while it is difficult, it is possible for determined non-state actors to acquire such capabilities and that such actors could conceivably implement nuclear terrorist strategies. The sixth section outlines the basic pathways to inadvertent inter-state nuclear war that have driven nuclear arms control and non-proliferation strategies for decades. The seventh section analyzes how states may lose control of nuclear weapons at critical moments in a nuclear confrontation, and how interaction between their nuclear control systems may itself play a role in leading to inadvertent nuclear war.
The eighth and concluding section argues that in circumstances of nuclear prone conflict and high levels of tension including threat of nuclear war, that a terrorist nuclear threat or attack could contribute to inadvertent nuclear war via a number of pathways. It is incumbent for nuclear armed and nuclear umbrella states to reduce the risk that such a trigger event could push states to nuclear first use, both by generally reducing tension and reliance on nuclear threats; and by anticipating how the fifth tier of non-state nuclear actors may erupt in surprising and massively disruptive ways in the midst of confrontations between nuclear weapons and umbrella states.
This essay covers a lot of terrain. Some may argue that it draws too long a bow, and exaggerates a risk that is so remote that it is not worth worrying about, especially compared with other risks of war and nuclear war in this region. Unfortunately, as Czeslaw Mesjasz notes, terrorist behavior falls between the purely chaotic and fully deterministic realms[1] and is fundamentally immune to top-down measures of surveillance and physical control. Under conditions of true complexity—as pertain today in the context of multiple forms of globalization and local displacement—it is not possible to predict specific outcomes, only to anticipate them and prepare for the best and the worst of possible worlds.
What is undeniable is that Northeast Asia is one of the regions most likely for states to come to nuclear blows, and that the trend in this region towards an increased risk of nuclear war. Although it is not a region routinely subject to mass casualty terrorism—unlike South Asia or the Middle East, arguably the other regional candidates for a terrorist-induced nuclear war today–Northeast Asia has a long history of terrorism including the most developed instance of nascent nuclear terrorism. Moreover, the global and local conditions that might lead to nuclear terrorism in this region are more pronounced today than in the past.
Given the possibility—to be demonstrated below—that a conjuncture between these two trends may exist in the future, and given the potentially existential cost of interstate nuclear war, it is urgent for states, market-based players, and civil society to start cooperating in Northeast Asia to reduce the risk that nuclear terrorism tips states over the nuclear brink into nuclear war.
Catalytic nuclear attack
Catalytic nuclear attack is a metaphor for the possible malevolent third party who sets out to induce a nuclear war between two other nuclear weapons states. It is based on a metaphor drawn from chemistry whereby a catalyst increases the rate of chemical reaction without catalyst itself being destroyed. Tiny amounts of a catalyst often suffice to bring about such a transformative effect.
Such a “catalytic” nuclear attack between nuclear weapons states was a serious policy concern in the nineteen-fifties in the United States where strategists were seized of the notion that a “small” nuclear weapons state (for which read “China”) could start a nuclear war between the United States and the former Soviet Union (FSU). As articulated by the ubiquitous Herman Kahn, the concern was that the small “catalytic” state instigating the conflict would be the least damaged at the end of a nuclear war, and could increase its relative power by starting a war between other nuclear armed states that resulted in their catastrophic destruction. In his classic essay outlining this argument, Donald Kobe derived what he termed to be suspicion, retaliation, destruction, catalytic war utility, and casualty matrices for each country that defined outcomes for each state in a “catalytic nuclear war.”[2]
As China began to test its own nuclear weapons and the United States and the FSU began to anticipate its deployment in the sixties, the ability of the two nuclear superpowers, even at this relatively early stage in their rapidly growing nuclear forces, to overwhelmingly retaliate and damage the catalytic state soon allayed this concern. Nonetheless, the concept motivated these two nuclear armed states to strive for nuclear non-proliferation, in part driven by their mutual fear of state-sponsored nuclear terrorism should nuclear weapons and nuclear weapons technology and materials become freely available—a concern that persisted over the subsequent decades.[3]
Is catalytic nuclear terrorism still a serious policy concern?
Today, the notion of “catalytic” nuclear war seems archaic in certain respects, and reflected a dismissive view at the time in the United States of the rationality of a state leadership armed with nuclear weapons and facing an overwhelming external adversary—in the case of China, not just one, but soon to be two external nuclear enemies that targeted its cities and nuclear forces. As China’s minimum deterrent posture evolved, and as its nuclear threat rhetoric subsided with the end of the Cultural Revolution, so the fear of catalytic nuclear war also receded. However, the fear of a catalytic nuclear war returned with a vengeance at the end of the Cold War when multiple states found themselves nuclear-armed almost overnight due to the collapse of the former Soviet Union, or proliferated independent nuclear forces in rapid succession in South Asia and in slow motion, North Korea.
In the United States and Russia, formal and informal discussion of the importance of avoiding war and nuclear war due to third party nuclear attack, by state or non-state actors, took place in diplomatic, military, and private channels, driven in part by the risk of nuclear “mega-terrorism” as the efforts of various insurgencies and global terrorist networks to acquire and use nuclear weapons came to light.
The continued salience of the concept of catalytic nuclear war rests on three nested arguments.
The first is that inadvertent nuclear war is possible, that is, the probability is greater than zero albeit unknowable. Multiple “threshold” events that could trigger inadvertent nuclear war are conceivable. In some unknowable combination, such drivers contribute to a probability greater than zero that nuclear war between states will occur, variously estimated at 0.1-1 percent year by strategic analysts—although there is no objective basis for such estimates, simply subjective estimates buttressed by the perception that specific near-nuclear wars punctuated the Cold War and post-Cold War decades, at which time the probability was perceived to be much higher for months at a time.
The second is that of all the drivers of inadvertent war, state-supported and non-state nuclear terrorism may be the least “directly controllable” by nuclear weapons states. Moreover, such nuclear terrorist attacks may coincide in the future with the influence of other drivers that could trigger rapid escalation to nuclear first use in conditions of complex nuclear confrontation involving two or more nuclear weapons states. Thus, the non-state terrorist driver of nuclear war may render “normal” positive and negative controls on nuclear use far less stabilizing than in the past when states were the sole concern in nuclear confrontations, depending on how a terrorist nuclear attack might affect the various contributing pathways to inadvertent nuclear war (listed in the next section).
The third is that such nuclear terrorist attacks may take many forms, as shown in Figure 1.
Figure 1: Types of Nuclear Terrorism from Least to Most Damaging

Notes to Figure 1: a credible threat not accompanied by one or more actions to realize the threat is the least damage act of terrorism, and rests on the perception of those threatened as to the perpetrator’s intention and capability. Many nuclear terrorism threats are made. Relatively few are credible. The types below “mere” threats are characterized by actions which may (or may not) have been preceded by credible threats. “Footloose” here is shorthand for loss of control of legitimate and authorized control entity, public or private, that is subject to diversion and seizure by a non-state entity. Cyber attacks may be part of the types of nuclear terrorism because a competent terrorist entity will employ cyberattacks as part of a nuclear terrorist attack. However, a cyber attack that disables critical infrastructure at the same time as another type of direct nuclear terrorist attack is conducted would be highly damaging and if it results of itself in mass casualties, may enable and amplify the consequences of dirty bomb or an actual nuclear detonation. In this sense, a cyber attack may be a cyber-multiplier for other types of nuclear terrorism. Of course, a cyber attack aimed at mass casualties and terrorist effects may be undertaken without any form of nuclear terrorism associated with it. Finally, acquisition of radioactive materials or fissile material may occur via theft, purchase, or self-manufacture (the least likely and most difficult of the three acquisition pathways). Some may argue that radiological weapons (dirty bombs) are not nuclear at all in that they do not involve criticality at all, just the radioactive properties of the materials, and may be relatively crude and low technology. However, some nuclear weapons aim to achieve precisely such radiological effects on varying scales and long-term radiological effects, rather than blast and other direct irradiation of targeted humans. Dirty bombs and nuclear bombs exist on a spectrum and where competent, malevolent, and motivated non-state actors might position themselves on that spectrum remains an open question.
***
These many types of terrorist nuclear attack present states with starkly different potential damage, greater possible ambiguity or even opacity in terms of precursor indicators as well as identity of the perpetrator. Any of these types of attack may affect nuclear-armed states in unpredictable ways with respect to their own nuclear use decisions at times when inter-state conflict may be more or less likely. These various types of attack by non-state actors reduce into three basic categories of threat and use, as follows:
- Credible threat of either nuclear detonation or radiological attack with possible massive damages
- Actual or sub-critical nuclear detonation
- Actual spent fuel or reactor attack with substantial radiological release.
In turn, such categories of terrorist attack might be realized in or against one or more types of targeted state, viz, a nuclear armed state, a nuclear umbrella state that receives nuclear extended deterrence from a nuclear armed state, or a non-nuclear weapons state which may or may not have nuclear fuel cycle facilities in and/or fissile material stored on its territory. (Thus, the target may or may not be a state, a state agency, or a state facility—it might be a civilian target such as a company or a religious entity; but in this paper, all terrorist nuclear attacks are assumed to take place only in places controlled by functioning states).
Nuclear terrorism post-cold war: trigger for inadvertent nuclear war?
The possible catalytic effect of nuclear terrorism on the risk of state-based nuclear war is not a simple linkage. The multiple types and scales of nuclear terrorism may affect state-nuclear use decisions along multiple pathways that lead to inadvertent nuclear war. These include:
- Early warning systems fail or are “tripped” in ways that lead to launch-on-warning
- Accidental nuclear detonation, including sub-critical explosions.
- Strategic miscalculation in crisis, show of force
- Decision-making failure (such as irrational, misperception, bias, degraded, group, and time-compressed decision-making)
- Allied or enemy choices (to seek revenge, to exploit nuclear risk, to act out of desperation)
- Organizational cybernetics whereby a nuclear command-control-and communications (NC3) system generates error, including the interplay of national NC3 systems in what may be termed the meta-NC3 system.
- Synchronous and coincident combinations of above.[4]
Exactly how, where, and when nuclear terrorism may “ambush” nuclear armed states already heading for or on such a path to inadvertent nuclear war depends on who is targeting whom at a given time, either immediately due to high tension, or generally due to a structural conflict between states. Nuclear armed states today form a complex set of global threat relationships that are not distributed uniformly across the face of Earth. Rather, based on sheer firepower and reach, the nine nuclear weapons states form a global hierarchy with at least four tiers, viz:
Tier 1: United States, clear technological supremacy and qualitative edge.
Tier 2: Russia, China, global nuclear powers and peers with the United States due to the unique destructive power of even relatively small nuclear arsenals, combined with global reach of missile and bomber delivery systems, thereby constituting a two-tiered global “nuclear triangle” with the United States.
Tier 3: France, UK, NATO nuclear sharing and delivery NATO members (Belgium, Germany, Italy, the Netherlands and Turkey) and the NATO and Pacific nuclear umbrella states (Japan, South Korea, Australia) that depend on American nuclear extended deterrence and directly and indirectly support US and US-allied nuclear operations even though they do not host nor deliver nuclear weapons themselves.
Tier 4: India, Pakistan, Israel, DPRK.
The first two tiers constitute the global nuclear threat triangle that exists between the United States, Russia, and China, forming a global nuclear “truel.” Each of these states targets the others; each represents an existential threat to the other; and each has a long history of mutual nuclear threat that is now a core element of their strategic identity.
Tier three consists of states with their own nuclear force but integrated with that of the United States (even France!) that expand the zone of mutual nuclear threat over much of the northern and even parts of the southern hemisphere; and states that host American nuclear command, control, communications, and intelligence systems that support US nuclear operations and to whom nuclear deterrence is “extended” (if, for example, Australia’s claim to having an American nuclear umbrella is believed). The fourth tier is composed of smaller nuclear forces with a primarily regional reach and focus.
Between most of these nuclear armed states and across the tiers, there are few shared “rules of the road.” The more of these states that are engaged in a specific conflict and location, the more unpredictable and unstable this global nuclear threat system becomes, with the potential for cascading and concatenating effects. Indeed, as the number of nuclear states projecting nuclear threat against each other increases, the notion of strategic stability may lose all meaning.
The emergence of a fifth tier—of non-state actors with the capacity to project nuclear threat against nuclear-armed and nuclear umbrella states (although not only these states)—is a critically important possible catalytic actor in the new conditions of nuclear threat complexity that already exist today. Such a layer represents an “edge of chaos” where the attempts by nuclear armed states to exert absolute “vertical” control over the use of nuclear weapons confront the potential of non-state entities and even individuals (insiders) to engage in “horizontal” nuclear terrorism, presenting radically different control imperatives to the standard paradigm of organizational procedures, technical measures, and safeguards of various kinds. This tier is like the waves and tides on a beach that quickly surrounds and then causes sand castles to collapse.
In 2010, Robert Ayson reviewed the potential linkages between inter-state nuclear war and non-state terrorism. He concluded: “…[T]hese two nuclear worlds—a non-state actor nuclear attack and a catastrophic interstate nuclear exchange—are not necessarily separable. It is just possible that some sort of terrorist attack, and especially an act of nuclear terrorism, could precipitate a chain of events leading to a massive exchange of nuclear weapons between two or more of the states that possess them.”[5] How this linkage might unfold is the subject of the next sections of this essay.
Are non-state actors motivated and able to attempt nuclear terrorism?
A diverse set of non-state actors have engaged in terrorist activities—for which there is no simple or consensual definition. In 2011, there were more than 6,900 known extremist, terrorist and other organizations associated with guerrilla warfare, political violence, protest, organized crime and cyber-crime. Of these, about 120 terrorist and extremist groups had been blacklisted by the United Nations, the European Union and six major countries.[6]
Some have argued that the technical, organizational, and funding demanded for a successful nuclear attack, especially involving nuclear weapons, exceeds the capacity of most of the non-state actors with terrorist proclivities. Unfortunately, this assertion is not true, especially at lower levels of impact as shown in Figure 1; but even at the highest levels of obtaining authentic nuclear weapons capabilities, a small number of non-state actors already exhibit the motivation and possible capacity to become nuclear-armed.
Ellingsen suggests a useful distinction that nuclear terrorists may be impelled by two divergent motivations, as shown in Figure 2, creating “opportunistic” and “patient” profiles.[7] The requirements for an opportunist non-state nuclear terrorist tend towards immediate use and the search for short-term payoffs with only tactical levels of commitment; whereas the patient non-state nuclear terrorist is able and willing to sustain a long-term acquisition effort to deal a strategic blow to an adversary in a manner that could be achieved only with nuclear weapons.
Figure 2: Opportunist versus strategic nuclear terrorist motivation
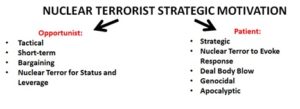
Source: S. Ellingsen, “Deliberations of a Nuclear Terrorist: Patience of Opportunism?” Defense & Security Analysis, 26:4, pp. 353-369 at: https://doi.org/10.1080/14751798.2010.534645
In turn, many factors will drive how a potential nuclear terrorist non-state organization that obtains nuclear weapons or materials may seek to employ them, especially in its nuclear command-and-control orientations.
Blair and Ackerman suggest that the goals, conditions, and capacity limitations that shape a possible nuclear terrorist’s posture lead logically to three types of nuclear terrorist nuclear command-and-control postures, viz: pre-determined (in which the leadership sends a fire order to a nuclear-armed subordinate and no change is entertained and no capacity to effect change is established in the field, that is, the order is fire-and-forget); assertive (in which only the central command can issue a nuclear fire order, central control is maintained at all times, with resulting demanding communications systems to support such control); and delegative (in which lower level commanders control nuclear weapons and have pre-delegated authority to use them in defined circumstances, for example, evidence of nuclear explosions combined with loss-of-connectivity with their central command).[8] An example of such delegative control system was the November 26, 2008 attack on Mumbai that used social media reporting to enable the attacking terrorists to respond to distant controller direction and to adapt to counter-terrorist attacks—a connectivity tactic that the authorities were too slow to shut down before mayhem was achieved.[9]
Logically, one might expect nuclear terrorists oriented toward short-term, tactical goals to employ pre-determined nuclear command-and-control strategies in the hope that the speed of attack and minimum field communications avoids discovery and interdiction before the attack is complete; whereas nuclear terrorists oriented toward long-term, strategic goals might employ more pre-delegative command-and-control systems that would support a bargaining use and therefore a field capacity to deploy nuclear weapons or materials that can calibrate actual attack based on communications with the central leadership with the risk of interdiction through surveillance and counter-attack. These differing strategic motivations, timelines, and strategies in many respects invert those of nuclear weapons states that rely on large organizations, procedures, and technical controls, to ensure that nuclear weapons are never used without legitimate authorization; and if they are used, to minimize needless civilian casualties (at least some nuclear armed states aspire to this outcome). The repertoire of state-based practices that presents other states with credible nuclear threat and reassures them that nuclear weapons are secure and controlled is likely to be completely mismatched with the strengths and strategies of non-state nuclear terrorists that may seek to maximize civilian terror, are not always concerned about their own survival or even that of their families and communities-of-origin, and may be willing to take extraordinary risk combined with creativity to exploit the opportunities for attack presented by nuclear weapons, umbrella, and non-nuclear states, or their private adversaries.
For non-state actors to succeed at complex engineering project such as acquiring a nuclear weapons or nuclear threat capacity demands substantial effort. Gary Ackerman specifies that to have a chance of succeeding, non-state actors with nuclear weapons aspirations must be able to demonstrate that they control substantial resources, have a safe haven in which to conduct research and development, have their own or procured expertise, are able to learn from failing and have the stamina and strategic commitment to do so, and manifest long-term planning and ability to make rational choices on decadal timelines. He identified five such violent non-state actors who already conducted such engineering projects (see Figure 3), and also noted the important facilitating condition of a global network of expertize and hardware. Thus, although the skill, financial, and materiel requirements of a non-state nuclear weapons project present a high bar, they are certainly reachable.
Figure 3: Complex engineering projects by five violent non-state actors & Khan network

Source: G. Ackerman, “Comparative Analysis of VNSA Complex Engineering Efforts,” Journal of Strategic Security, 9:1, 2016, at: http://scholarcommons.usf.edu/jss/vol9/iss1/10/
Along similar lines, James Forest examined the extent to which non-state actors can pose a threat of nuclear terrorism.[10] He notes that such entities face practical constraints, including expense, the obstacles to stealing many essential elements for nuclear weapons, the risk of discovery, and the difficulties of constructing and concealing such weapons. He also recognizes the strategic constraints that work against obtaining nuclear weapons, including a cost-benefit analysis, possible de-legitimation that might follow from perceived genocidal intent or use, and the primacy of political-ideological objectives over long-term projects that might lead to the group’s elimination, the availability of cheaper and more effective alternatives that would be foregone by pursuit of nuclear weapons, and the risk of failure and/or discovery before successful acquisition and use occurs. In the past, almost all—but not all—non-state terrorist groups appeared to be restrained by a combination of high practical and strategic constraints, plus their own cost-benefit analysis of the opportunity costs of pursuing nuclear weapons. However, should some or all of these constraints diminish, a rapid non-state nuclear proliferation is possible.
Although only a few non-state actors such as Al Qaeda and Islamic State have exhibited such underlying stamina and organizational capacities and actually attempted to obtain nuclear weapons-related skills, hardware, and materials, the past is not prologue. An incredibly diverse set of variously motivated terrorist groups exist already, including politico-ideological, apocalyptic-millenarian, politico-religious, nationalist-separatist, ecological, and political-insurgency entities, some of which converge with criminal-military and criminal-scientist (profit based) networks; but also pyscho-pathological mass killing cults, lone wolves, and ephemeral copy-cat non-state actors. The social, economic, and deculturating conditions that generate such entities are likely to persist and even expand.
In particular, rapidly growing coastal mega-cities as part of rapid global urbanization offer such actors the ability to sustain themselves as “flow gatekeepers,” possibly in alliance with global criminal networks, thereby supplanting the highland origins of many of today’s non-state violent actors with global reach.[11] Other contributing factors contributing to the supply of possible non-state actors seeking nuclear weapons include new entries such as city states in search of new security strategies, megacities creating their own transnationally active security forces, non-states with partial or complete territorial control such as Taiwan and various micro-states, failing states, provinces in dissociating, failing states that fall victim to internal chaos and the displacement effects of untrammeled globalization, and altogether failed states resulting in ungoverned spaces. To this must be added domestic terrorist entities in the advanced industrial states as they hollow out their economies due to economic globalization and restructuring, adjust to cross-border migration, and adapt to cultural and political dislocation.
In short, the prognosis is for the fifth tier of non-state actors to beset the other four tiers with intense turbulence just as waves on a beach swirl around sandcastles, washing away their foundations, causing grains of sand to cascade, and eventually collapsing the whole structure.
Observed non-state nuclear threats and attacks
In light of the constraints faced by non-state terrorist actors in past decades, it is not surprising that the constellation of actual nuclear terrorist attacks and threats has been relatively limited during and since the end of the Cold War. As Martha Crenshaw noted in a comment on the draft of this paper:
We still don’t know why terrorists (in the sense of non-state actors) have not moved into the CBRN [chemical,biological, radiological or nuclear ] domain. (Many people think biosecurity is more critical, for that matter.) Such a move would be extremely risky for the terrorist actor, even if the group possessed both capability (resources, secure space, time, patience) and motivation (willingness to expend the effort, considering opportunity costs). So far it appears that “conventional” terrorism serves their purposes well enough. Most of what we have seen is rhetoric, with some scattered and not always energetic initiatives.[12]
Nonetheless, those that have occurred demonstrate unambiguously that such threats and attacks are not merely hypothetical, in spite of the limiting conditions outlined above. One survey documented eighty actual, planned attacks on nuclear facilities containing nuclear materials between 1961-2016[13] as follows:
- 80 attacks in 3 waves (1970s armed assaults, 1990s thefts, post-2010, breaches)
- High threat attacks: 32/80 attacks posed substantial, verified threat of which 44 percent involved insiders.
- All types of targets were found in the data set—on reactors, other nuclear facilities, military bases leading Gary Ackerman and to conclude: “Overall, empirical evidence suggests that there are sufficient cases in each of the listed categories that no type of threat can be ignored.”[14]
No region was immune; no year was without such a threat or attack. Thus, there is a likely to be a coincidence of future non-state threats and attacks with inter-state nuclear-prone conflicts, as in the past, and possibly more so given the current trend in and the generative conditions for global terrorist activity that will likely pertain in the coming decades.
Of these attacks, about a quarter each were ethno-nationalist, secular utopian, or unknown in motivation; and the remaining quarter were a motley mix of religious (11 percent), “other” (5 percent), personal-idiosyncratic (4 percent), single issue (2 percent) and state sponsored (1 percent) in motivation.
The conclusion is unavoidable that there a non-state nuclear terrorist attack in the Northeast Asia region is possible. The following sections outline the possible situations in which nuclear terrorist attacks might be implicated as a trigger to interstate conflict, and even nuclear war. Particular attention is paid to the how nuclear command, control and communications systems may play an independent and unanticipated role in leading to inadvertent nuclear war, separate to the contributors to inadvertency normally included such as degradation of decision-making due to time and other pressures; accident; “wetware” (human failures), software or hardware failures; and misinterpretation of intended or unintended signals from an adversary.
Regional pathways to interstate nuclear war
At least five distinct nuclear-prone axes of conflict are evident in Northeast Asia. These are:
- US-DPRK conflict (including with United States, US allies Japan, South Korea and Australia; and all other UNC command allies. Many permutations possible ranging from non-violent collapse to implosion and civil war, inter-Korean war, slow humanitarian crisis. Of these implosion-civil war in the DPRK may be the most dangerous, followed closely by an altercation at the Joint Security Area at Panmunjon where US, ROK, and DPRK soldiers interact constantly.
- China-Taiwan conflict, whereby China may use nuclear weapons to overcome US forces operating in the West Pacific, either at sea, or based on US (Guam, Alaska) or US allied territory in the ROK, Japan, the Philippines, or Australia); or US uses nuclear weapons in response to Chinese attack on Taiwan.
- China-Japan conflict escalates via attacks on early warning systems, for example, underwater hydrophone systems (Ayson-Ball, 2011).
- China-Russia conflict, possibly in context of loss-of-control of Chinese nuclear forces in a regional conflict involving Taiwan or North Korea.
- Russia-US conflict, involving horizontal escalation from a head-on collision with Russian nuclear forces in Europe or the Middle East; or somehow starts at sea (mostly likely seems ASW) or over North Korea (some have cited risk of US missile defenses against North Korean attack as risking Russian immediate response).
Combinations of or simultaneous eruption of the above conflicts that culminate in nuclear war are also possible. Other unanticipated nuclear-prone conflict axes (such as Russia-Japan) could also emerge with little warning.
Precursors of such nuclear-laden conflicts in this region also exist that could lead states to the brink of nuclear war and demonstrate that nuclear war is all too possible between states in this region. Examples include the August 1958 Quemoy-Matsu crisis, in which the United States deployed nuclear weapons to Taiwan, and the US Air Force has only a nuclear defense strategy in place to defend Taiwan should China have escalated its shelling campaign to an actual attack; the October 1962 Cuban Missile Crisis, when a US nuclear armed missile was nearly fired from Okinawa due to a false fire order; the March 1969 Chinese-Soviet military clash and resulting consideration of nuclear attacks by both sides; and the August 1976 poplar tree crisis at Panmunjon in Korea, when the United States moved nuclear weapons back to the DMZ and the White House issued pre-delegated orders to the US commander in Korea to attack North Korea if the tree cutting task force was attacked by North Korean forces.
Loss-of-control of Nuclear Weapons
As is well known, nuclear armed states must routinely—and in the midst of a crisis—ensure that their nuclear weapons are never used without legitimate authority, but also ensure at the same time that they are always available for immediate use with legitimate authority. This “always-never” paradox is managed in part by a set of negative and positive controls, reliant upon procedural and technical measures, to maintain legitimate state-based command-and-control (see Figure Four).
Figure Four: Controls and Measures on Nuclear Weapons Use
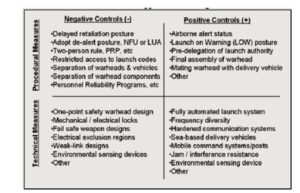
Source: Virginia Tech Applied Research Corporation, Nuclear Command, Control, and Stability Framework, December 29, 2016, at: https://calhoun.nps.edu/bitstream/handle/10945/48707/Nuclear%20Command%20Control%20and%20Stability%20Assessment_Final%20report_29Dec15%20rev2.pdf?sequence=1&isAllowed=y
In this framework, Jerry Conley has produced a taxonomy of nuclear command-and-control structures that embody varying notional national “command-and-control” orientations (also referred to as stability points or biases). Each nuclear armed state exhibits a distinct preference for technical and procedural measures to achieve negative and positive control of nuclear weapons. The way that a state constructs its control system varies depending on its size, wealth, technology, leadership, and strategic orientation, lending each state a unique use propensity affected by the information processing and transmission functions of the nuclear command-and-control system, that in part determines the use or non-use decisions made by the leaders of nuclear armed states. The resulting ideal nuclear command-and-control state structures are shown in Table 1.
Table 1: Ideal Nuclear command-and-control structures
|
Wealthy |
A nuclear program that has economic resources to research, expand, and bolster itself with both experienced people and technical innovations. |
|
Poor |
A nuclear program that does not have sufficient economic resources to properly research, expand, and bolster itself and relies on procedures instead of technology and experience. |
|
Complex |
A nuclear program that has the material resources and personnel to support a wide range of controls and redundancies. |
|
Simple |
A nuclear program that has minimal material resources or personnel to adequately support a robust and redundant C2 structure. |
|
Centralized |
A nuclear program that maintains authority and control of its nuclear armament as a singular capability through a defined chain of command. |
|
Decentralized |
A nuclear program that distributes authority of its nuclear armament to a network of commanders or individuals who operate as independent decision makers with minimal oversight. |
|
Civilian |
A nuclear program that is governed by an elected, non-military government that maintains authority and control over the nuclear arsenal through a defined chain of authority. |
|
Military |
A nuclear program that is governed by a weak civilian government and/or the military maintains control and authority over the nuclear arsenal. |
Source: Virginia Tech Applied Research Corporation, Nuclear Command, Control, and Stability Framework, December 29, 2016, at: https://calhoun.nps.edu/bitstream/handle/10945/48707/Nuclear%20Command%20Control%20and%20Stability%20Assessment_Final%20report_29Dec15%20rev2.pdf?sequence=1&isAllowed=y
These ideal types are summarized with respect to the defining axes of control measure in Figure Five.
Figure Five: State nuclear weapons control biases by NC3 type
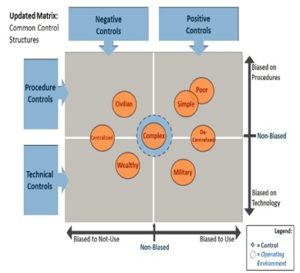
Note: according to dominant characteristic shown in orange circle; also, real states may exhibit more than one characteristic
Source: Virginia Tech Applied Research Corporation, Nuclear Command, Control, and Stability Framework, December 29, 2016, at: https://calhoun.nps.edu/bitstream/handle/10945/48707/Nuclear%20Command%20Control%20and%20Stability%20Assessment_Final%20report_29Dec15%20rev2.pdf?sequence=1&isAllowed=y
In Northeast Asia, a four-way nuclear threat system exists that has a three world-class nuclear armed states, the United States, Russia and China, interacting with a fourth tier, barely nuclear armed state, the DPRK. In this quadrilateral nuclear standoff, the DPRK’s simple NC3 system likely is an amalgam of a poorly resourced, militarized, and personalized leadership—which may lead it to oscillate between procedural and technical measures as the basis of control, with a primary emphasis on positive use control, not negative control to avoid unauthorized use. China’s large, centralized NC3 system co-mingles nuclear and conventional communications between national commanders and deployed nuclear forces and may emphasize negative more than positive use controls to ensure Party control. Russia’s highly centralized, complex NC3 system relies on legacy technology and limited economic base for modernization. It too may be more oriented towards negative controls in peacetime, but have the capacity to spring almost instantly to primary reliance on positive controls in times of crisis or tension. The US NC3 system is large, complex and based on wealth and technological prowess. It is under civilian, not military control, at least in principle and in peacetime, and is redundant, diverse, and relatively resilient.
Non-state nuclear attack as trigger of inter-state nuclear war in Northeast Asia
The critical issue is how a nuclear terrorist attack may “catalyze” inter-state nuclear war, especially the NC3 systems that inform and partly determine how leaders respond to nuclear threat. Current conditions in Northeast Asia suggest that multiple precursory conditions for nuclear terrorism already exist or exist in nascent form. In Japan, for example, low-level, individual, terroristic violence with nuclear materials, against nuclear facilities, is real. In all countries of the region, the risk of diversion of nuclear material is real, although the risk is likely higher due to volume and laxity of security in some countries of the region than in others. In all countries, the risk of an insider “sleeper” threat is real in security and nuclear agencies, and such insiders already operated in actual terrorist organizations. Insider corruption is also observable in nuclear fuel cycle agencies in all countries of the region. The threat of extortion to induce insider cooperation is also real in all countries. The possibility of a cult attempting to build and buy nuclear weapons is real and has already occurred in the region.[15] Cyber-terrorism against nuclear reactors is real and such attacks have already taken place in South Korea (although it remains difficult to attribute the source of the attacks with certainty). The stand-off ballistic and drone threat to nuclear weapons and fuel cycle facilities is real in the region, including from non-state actors, some of whom have already adopted and used such technology almost instantly from when it becomes accessible (for example, drones).[16]
Two other broad risk factors are also present in the region. The social and political conditions for extreme ethnic and xenophobic nationalism are emerging in China, Korea, Japan, and Russia. Although there has been no risk of attack on or loss of control over nuclear weapons since their removal from Japan in 1972 and from South Korea in 1991, this risk continues to exist in North Korea, China, and Russia, and to the extent that they are deployed on aircraft and ships of these and other nuclear weapons states (including submarines) deployed in the region’s high seas, also outside their territorial borders.
The most conducive circumstance for catalysis to occur due to a nuclear terrorist attack might involve the following nexi of timing and conditions:
- Low-level, tactical, or random individual terrorist attacks for whatever reasons, even assassination of national leaders, up to and including dirty radiological bomb attacks, that overlap with inter-state crisis dynamics in ways that affect state decisions to threaten with or to use nuclear weapons. This might be undertaken by an opportunist nuclear terrorist entity in search of rapid and high political impact.
- Attacks on major national or international events in each country to maximize terror and to de-legitimate national leaders and whole governments. In Japan, for example, more than ten heads of state and senior ministerial international meetings are held each year. For the strategic nuclear terrorist, patiently acquiring higher level nuclear threat capabilities for such attacks and then staging them to maximum effect could accrue strategic gains.
- Attacks or threatened attacks, including deception and disguised attacks, will have maximum leverage when nuclear-armed states are near or on the brink of war or during a national crisis (such as Fukushima), when intelligence agencies, national leaders, facility operators, surveillance and policing agencies, and first responders are already maximally committed and over-extended.
At this point, we note an important caveat to the original concept of catalytic nuclear war as it might pertain to nuclear terrorist threats or attacks. Although an attack might be disguised so that it is attributed to a nuclear-armed state, or a ruse might be undertaken to threaten such attacks by deception, in reality a catalytic strike by a nuclear weapons state in conditions of mutual vulnerability to nuclear retaliation for such a strike from other nuclear armed states would be highly irrational.
Accordingly, the effect of nuclear terrorism involving a nuclear detonation or major radiological release may not of itself be catalytic of nuclear war—at least not intentionally–because it will not lead directly to the destruction of a targeted nuclear-armed state. Rather, it may be catalytic of non-nuclear war between states, especially if the non-state actor turns out to be aligned with or sponsored by a state (in many Japanese minds, the natural candidate for the perpetrator of such an attack is the pro-North Korean General Association of Korean Residents, often called Chosen Soren, which represents many of the otherwise stateless Koreans who were born and live in Japan) and a further sequence of coincident events is necessary to drive escalation to the point of nuclear first use by a state. Also, the catalyst—the non-state actor–is almost assured of discovery and destruction either during the attack itself (if it takes the form of a nuclear suicide attack then self-immolation is assured) or as a result of a search-and-destroy campaign from the targeted state (unless the targeted government is annihilated by the initial terrorist nuclear attack).
It follows that the effects of a non-state nuclear attack may be characterized better as a trigger effect, bringing about a cascade of nuclear use decisions within NC3 systems that shift each state increasingly away from nuclear non-use and increasingly towards nuclear use by releasing negative controls and enhancing positive controls in multiple action-reaction escalation spirals (depending on how many nuclear armed states are party to an inter-state conflict that is already underway at the time of the non-state nuclear attack); and/or by inducing concatenating nuclear attacks across geographically proximate nuclear weapons forces of states already caught in the crossfire of nuclear threat or attacks of their own making before a nuclear terrorist attack.[17]
An example of a cascading effect would be a non-state attack on a key node of linked early warning systems that is unique to and critical for strategic nuclear forces to be employable, or the effect of multiple, coincident and erroneous sensor alerts of incoming attacks (as occurred during the Cuban Missile Crisis with radar in Florida monitoring Soviet missiles in Cuba that mistakenly fused an erroneous reading of a missile trajectory with a real observation of a Soviet satellite that happened to be passing overhead).
An example of a concatenating effect would an attack that leads a nuclear weapons state to target two other states forces because it cannot determine whose forces attacked its own. This circumstance might arise if key anti-submarine forces or an aircraft carrier battle group were attacked and it was impossible to determine in a given waterway or area of ocean whose submarines were present or responsible for the attack, leading the attacked state to destroy all the submarines presenting on-going threat to its strategic forces.
As we noted above, a terrorist nuclear shock may take various forms and appear in different places. Ever since an extortion attempt in Boston in 1974 based on the threat of nuclear detonation, the threat of an improvised nuclear device has been credible. For such a threat to be credible, a non-state terrorist entity must release a plausible precursor such as nuclear material or warhead design information, or stage an actual demonstration attack that makes it plausible that the attacker controls a significant quantity of fissile material (most likely plutonium, or simply radioactive materials suitable for a radiological device that might be used to draw in first responders and then detonate a warhead to maximize damage and terror). Such an attack might be combined with a separate attack on critical infrastructure such as a cyberattack. The attacker might retain sufficient material for bargaining and insurance should the initial attack fail. Given the need to adapt to circumstances, such an attacker is likely to be patient and strategic, in the terms defined earlier, and to have extensive organizational and communication capacities; and to be able to operate at multiple targeted sites, possibly in multiple countries. Given its patience and stamina, such an attacker would select a highly symbolic target such as a high level meeting. Such a case would present the targeted state with an exquisite dilemma: bargaining and negotiation with the non-state actor threatening such an attack may be justified given the explicit and plausible nature of the threat, which may be politically impossible while making counter-terrorism operations very risky and only possible with extreme caution. And, such an attacker might well issue a false statement about state-sponsorship to invoke third parties in ways that vastly complicate the response to the threat.
If the attacker is less capable and driven for immediate political or other returns, then it may be satisfied with highly delegated delivery with no recall option, and no use of communications to minimize the risk of discovery or interdiction. Such an attacker is also less likely to wait for the circumstances in which inter-state nuclear war is more likely due to inter-state tension; and also less likely to seek third party effects beyond the damage to the immediate target and resulting terror. Should surveillance indicate that an improvised nuclear device is in motion, then an all-out search to interdict the attackers and to retrieve the device or materials would likely ensue.
In these two instances of credible threat of non-state nuclear attack, the insider versus outsider perpetrator factor will affect significantly how the attack affects possible inter-state conflicts. In Kobe’s terms, if the perpetrator is confirmed to be an outsider, then a country-of-origin suspicion matrix may cast suspicion onto another state as possible sponsor. For an attack threatened in China, the linkage might be back to Russia, the United States, or North Korea. For an attack threatened in Russia, the linkage might be back to the United States, China, or North Korea. For an attack threatened in North Korea, the linkage might be back to the United States, China, or Russia. And for an attack threatened in one of the umbrella states in the region, South Korea and Japan, such an attack might be linked to each other, as well as to China, North Korea, or Russia. In each case, the shadow of suspicion and possible accusations could tilt decision-making processes in one or more of these states and ways that could worsen pre-existing views about the nuclear use propensity of an opposing nuclear armed state.
Should an actual nuclear attack occur, the situation is even more complex and problematic. Such an attack might be purely accidental, due to hardware, software, or human error while nuclear materials or weapons are in transit. In principle, this limits the site of such an event to the nuclear weapons states or their ships and aircraft as neither South Korea nor Japan host nuclear weapons today. If an insider is involved, then the perpetrator may be identified quickly, and whether there is a linkage with another state may become evident (depending on nuclear forensics as well as insight obtained from surviving attackers).
If an outsider is the perpetrator, then the suspicion matrix will come into play again, with possibly severe effects on inter-state tension due to accusation, suspicion, and fear of follow-on attacks. During the attack, especially if it is a hostage-taking type of attack, the identity of the perpetrator may be unknown or ambiguous, and maintaining this ambiguity or even opacity as to the attacker may be deliberate—as was the case with the 2008 Mumbai attack in which the controller tried to ensure that all the attackers were killed in the course of the twelve separate but coordinated attacks across the city over four days. Although much progress has been made in establishing local nuclear forensics capability in Japan,[18] China, and South Korea, there is no certainty that it is sufficiently developed to identify the perpetrator of an act of nuclear terrorism, especially if there is a state sponsor and deception involved.
Conclusion
We now move to our conclusion. Nuclear-armed states can place themselves on the edge of nuclear war by a combination of threatening force deployments and threat rhetoric. Statements by US and North Korea’s leaders and supporting amplification by state and private media to present just such a lethal combination. Many observers have observed that the risk of war and nuclear war, in Korea and globally, have increased in the last few years—although no-one can say with authority by how much and exactly for what reasons.
However, states are restrained in their actual decisions to escalate to conflict and/or nuclear war by conventional deterrence, vital national interests, and other institutional and political restraints, both domestic and international. It is not easy, in the real world, or even in fiction, to start nuclear wars.[19] Rhetorical threats are standard fare in realist and constructivist accounts of inter-state nuclear deterrence, compellence, and reassurance, and are not cause for alarm per se. States will manage the risk in each of the threat relationships with other nuclear armed states to stay back from the brink, let alone go over it, as they have in the past.
This argument was powerful and to many, persuasive during the Cold War although it does not deny the hair-raising risks taken by nuclear armed states during this period. Today, the multi-polarity of nine nuclear weapons states interacting in a four-tiered nuclear threat system means that the practice of sustaining nuclear threat and preparing for nuclear war is no longer merely complicated, but is now enormously complex in ways that may exceed the capacity of some and perhaps all states to manage, even without the emergence of a fifth tier of non-state actors to add further unpredictability to how this system works in practice.
The possibility that non-state actors may attack without advance warning as to the time, place, and angle of attack presents another layer of uncertainty to this complexity as to how inter-state nuclear war may break out. That is, non-state actors with nuclear weapons or threat goals and capacities do not seek the same goals, will not use the same control systems, and will use radically different organizational procedures and systems to deliver on their threats compared with nuclear armed states. If used tactically for immediate terrorist effect, a non-state nuclear terrorist could violently attack nuclear facilities, exploiting any number of vulnerabilities in fuel cycle facility security, or use actual nuclear materials and even warheads against military or civilian targets. If a persistent, strategically oriented nuclear terrorist succeed in gaining credible nuclear threat capacities, it might take hostage one or more states or cities.
If such an event coincides with already high levels of tension and even military collisions between the non-nuclear forces of nuclear armed states, then a non-state nuclear terrorist attack could impel a nuclear armed state to escalate its threat or even military actions against other states, in the belief that this targeted state may have sponsored the non-state attack, or was simply the source of the attack, whatever the declared identity of the attacking non-state entity. This outcome could trigger these states to go onto one or more of the pathways to inadvertent nuclear war, especially if the terrorist attack was on a high value and high risk nuclear facility or involved the seizure and/or use of fissile material.
Some experts dismiss this possibility as so remote as to be not worth worrying about. Yet the history of nuclear terrorism globally and in the Northeast Asian region suggests otherwise. Using the sand castle metaphor, once built on the high tide line, sand castles may withstand the wind but eventually succumb to the tide once it reaches the castle—at least once, usually twice a day. Also, theories of organizational and technological failure point to the coincidence of multiple, relatively insignificant driving events that interact or accumulate in ways that lead the “metasystem” to fail, even if each individual component of a system works perfectly. Thus, the potential catalytic effect of a nuclear terrorist incident is not that it would of itself lead to a sudden inter-state nuclear war; but that at a time of crisis when alert levels are already high, when control systems on nuclear forces have already shifted from primary emphasis on negative to positive control, when decision making is already stressed, when the potential for miscalculation is already high due to shows of force indicating that first-use is nigh, when rhetorical threats promising annihilation on the one hand, or collapse of morale and weakness on the other invite counter-vailing threats by nuclear adversaries or their allies to gain the upper hand in the “contest of resolve,” and when organizational cybernetics may be in play such that purposeful actions are implemented differently than intended, then a terrorist nuclear attack may shift a coincident combination of some or all of these factors to a threshold level where they collectively lead to a first-use decision by one or more nuclear-armed states. If the terrorist attack is timed or happens to coincide with high levels of inter-state tension involving nuclear-armed states, then some or all of these tendencies will likely be in play anyway—precisely the concern of those who posit pathways to inadvertent nuclear war as outlined in section 2 above.
The critical question is, just as a catalyst breaks some bonds and lets other bonds form, reducing the energy cost and time taken to achieve a chemical reaction, how would a nuclear terrorist attack at time of nuclear charged inter-state tension potentially shift the way that nuclear threat is projected and perceived in a four or five-way nuclear-prone conflict, and how might it affect the potential pathways to inadvertent nuclear war in such a system?
Such a pervasive incremental effect is shown in Figure 6 below.
Figure 6: Impact of a Terrorist Nuclear Threat or Attack on Interstate Nuclear Use Control
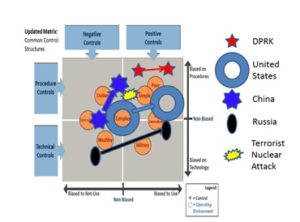
Any one or indeed all of these starting nuclear control profiles may be disputed, as might the control profile at the end of the response arrow. (In Figure 6, each nuclear state responds to a terrorist nuclear attack by loosening or abandoning negative controls against unauthorized use, and shifts towards reliance mostly on positive procedural controls biased towards use). But each nuclear armed state will make its moves in response to the posited terrorist nuclear attack partly in response to its expectations as to how other nuclear armed states will perceive and respond to these moves, as well as their perception that an enemy state may have sponsored a terrorist nuclear attack—and considered together, it is obvious that they may not share a common image of the other states’ motivations and actions in this response, leading to cumulative potential for misinterpretation and rapid subsequent action, reaction, and escalation.
It is also conceivable—although intuitively it would seem far less likely–that a terrorist nuclear attack at such a conjuncture of partly or fully mobilized nuclear armed states might induce one or more of them to stand down, slow down its decision making or deployments, establish new communication channels with potential nuclear enemy states, and even make common cause to hunt down and eliminate the non-state nuclear terrorist entity, or coordinate operations to respond to the threat of a second terrorist nuclear attack—the credibility of which would be high in the aftermath of a successful initial non-state nuclear attack.
As Robert Ayson concluded:
In considering the ways in which a terrorist nuclear attack could (wittingly or unwittingly) spark off a wider nuclear exchange government leaders are entitled to be just as worried about their own actions—how they would respond to a terrorist nuclear attack and how that response might get very catastrophically out of control—as about the terrorist act per se. If so, states need to do more than consider the best ways to prevent terrorists from acquiring, deploying and then detonating a nuclear weapon. They also need to think about how they can control themselves in the event of a nuclear terrorist attack (even if some might suggest this risks handing the terrorist a premature and unnecessary victory by giving them indirect influence over the choices states make).[20]
Thus, it would make sense for nuclear armed and umbrella states in the region, individually and collectively, to consider measures that reduce the susceptibility of the inter-state nuclear threat system to effects of non-state nuclear terrorism, viz:
- Averting and ameliorating confrontation between nuclear weapons states, by promulgating and implementing a regional comprehensive security framework in Northeast Asa;
- Establishing a regional framework that reduces reliance upon and enables states to manage nuclear threats in an explicit and legally defined manner (a nuclear weapons-free zone is the obvious structure);
- Creating a regional risk reduction center and implementing far greater transparency on the location, numbers, and types of nuclear weapons, to reduce the potential for mistaken perceptions and countervailing force deployments.
- Recessing nuclear threat in national declaratory and operational doctrines, deployments, and practices.
- Adopting norms of not using nuclear weapons first and exploring ways for nuclear weapons states to harmonize and upgrade their nuclear command-and-control systems.
- Developing and implementing strong negative control measures on nuclear weapons to reduce the risk of inadvertent nuclear war due to loss of control over nuclear weapons
These measures are at the level of maintaining the integrity of the sandcastles themselves.
At the level of the beach sand and tides, a range of measures that might delink inter-state nuclear war and nuclear terrorist attack should be considered by states in the region. These include:
- Commencing regional cooperation to reduce the vulnerability to non-state actor attacks on nuclear forces and/or nuclear facilities, and for a well-tested communication system as well as concerted, coordinated, and collaborative political, emergency, and military response to the threat or event of nuclear terrorist attack.
- Establishing regional “weak link” and “small world” networks of nuclear security and counter-terrorism experts and practitioners, including the DPRK, to promote mutual learning and comprehension of this unconventional threat.
- Activating city and critical infrastructure facility-based “glocal” intelligence networks.
- Conducting regional table-top exercises on regional and global terrorist scenarios
- Accelerating regional and national shift to spent fuel dry cask storage, and de-densification of spent fuel pools to make them unattractive targets for attack or hostage-taking.
- Reducing the quanta and availability of separated nuclear materials and radiological targets.
- Strengthening nuclear attribution and forensics capabilities to reduce crisis ambiguity.
- Conducting smuggling/transport/terrorism route analysis into, out of and within region.
- Strengthening nuclear facility personnel reliability programs in all countries of the region, and harmonizing standards for personnel reliability.
- Increase regional coordination to interdict transnational, cross-border criminal networks that may converge with terrorists as suppliers or implementors of nuclear terrorism.
- Enhance cyber cooperation against cyber crime and cyber warfare against critical infrastructure in the region.
- Increase site protection against drones, especially in nuclear materials sites.
III. ENDNOTES
[1] Czeslaw Mesjasz, “Complex Systems Studies and Terrorism,” in P.V. Fellman et al. (eds.), Conflict and Complexity, Understanding Complex Systems, Springer, New York, 2015, p. 62, at: http://lawsdocbox.com/66070780-Politics/Chapter-2-complex-systems-studies-and-terrorism.html
[2] Donald Kobe, “A Theory of Catalytic War,” The Journal of Conflict Resolution, 6:2, June 1962, pp. 125-142, at: http://www.jstor.org/stable/172987
[3] J. Digby et al, How Nuclear War Might Start, Scenarios from the 21st Century, RAND Note N-2614-NA, Santa Monica, October 1988, at: https://www.rand.org/content/dam/rand/pubs/notes/2009/N2614.pdf
[4] This list is drawn from H. Wiberg, I.D. Peterson, P. Smoker, ed, Inadvertent Nuclear War: The Implications of the Changing Global Order, Pergamon, 1993.
[5] Robert Ayson, “After a Terrorist Nuclear Attack: Envisaging Catalytic Effects,” Studies in conflict and terrorism, 33:7, 2010, p. 584, at: http://www.tandfonline.com/doi/abs/10.1080/1057610X.2010.483756
[6] Albert J. Jongman, “Introduction To The World Directory Of Extremist, Terrorist And Other Organisations Associated With Guerrilla Warfare, Political Violence, Protest, Organised Crime And Cyber-Crime,” in A. Schmid, edited, The Routledge Handbook of Terrorism Research , Taylor and Francis, Kindle Edition, 2011.
[7] S. Ellingsen, “Deliberations of a Nuclear Terrorist: Patience of Opportunism?” Defense & Security Analysis, 26:4, pp. 353-369 at: https://doi.org/10.1080/14751798.2010.534645
[8] C. Blair, G. Ackerman, Radiological and Nuclear Adversary Project, Task 3: Terrorist Nuclear Command and Control, National Consortium for the Study of Terrorism and Responses to Terrorism, Maryland, July 25, 2012, pp. 21 et passim, at: fas.org/irp/threat/tncc.pdf
[9] S. Azad, A. Gupta, “A Quantitative Assessment on 26/11 Mumbai Attack using Social Network Analysis,” Journal of Terrorism Research, 2:2 October 2011, at: http://jtr.st-andrews.ac.uk/articles/10.15664/jtr.187/
[10] J. Forest, “Framework for Analyzing the Future Threat of WMD Terrorism,” Journal of Strategic Security, 5:4, 2012, pp. 61-62, at: http://scholarcommons.usf.edu/jss/vol5/iss4/9
[11] David Killcullen Out of the Mountains: The Coming Age of the Urban Guerrilla. New York: Oxford University Press. 2013; a summary is found in his The Australian Army in the Urban, Networked Littoral, Army Research Paper 2, The Australian Army, 2014, at: https://www.army.gov.au/sites/g/files/net1846/f/kilcullen_11august.pdf
[12] Martha Crenshaw, personal communication by email, December 16, 2017.
[13] Gary Ackerman; Charles Blair; Maranda Sorrells, 2011, “Radiological and Nuclear Non-State Adversaries Database (RANNSAD)”, hdl:1902.1/16258, Harvard Dataverse, http://www.start.umd.edu/data-tools/nuclear-facility-attack-database
Nuclear Facility Attack Database (NuFAD), March 2016 at: http://www.start.umd.edu/sites/default/files/files/NFADSourceListMar2016.pdf and
Gary Ackerman, Jeffrey M. Bale, Charles P. Blair, et al, Assessing Terrorist Motivations for Attacking Critical Infrastructure, Lawrence Livermore National Laboratory, UCRL-TR-227068, December 4, 2006, 16-18, available at: https://e-reports-ext.llnl.gov/pdf/341566.pdf
[14] G. Ackerman, James Halverson, “Attacking nuclear facilities: hype or genuine threat?” pp. 142-191, in B. Volders, T. Sauer, Nuclear Terrorism, Countering the Threat, Routledge, 2016
[15] Aum Shinrikyo’s attempts to obtain nuclear weapons via placement of its operatives in positions in the nuclear industry in Japan, to obtain uranium from Australia, etc. did not manifest a realistic capability to acquire nuclear weapons from its own technical capacities. However, a cult operative known to have wanted to buy a nuclear warhead visited Moscow multiple times in 1994 with $15 million in cash at a time when Russia’s nuclear complex was in post-Soviet chaos was a serious attempt to gain actual capability and demonstrates the seriousness of their commitment and depth of their capacity to pursue this option. Aum leaders had previously cultivated black market players in Russia from 1992 onwards. According to the RAND report cited below, it also targeted Russia’s “premier nuclear research facility, the Kurchatov Institute, for expertise and technology because it reportedly possessed hundreds of kilograms of weapons-usable uranium.” See S. Daly, J. Parachini, W. Rosenau, Aum Shinrikyo, Al Qaeda, and the Kinshasa Reactor, Implications of Three Case Studies for Combating Nuclear Terrorism, RAND Documented Briefing, Santa Monica, 2005, pp. 11-14, at: https://www.rand.org/pubs/documented_briefings/DB458.html
[16] These risks are reviewed in detail in the Special Reports from the Reducing Risk of Nuclear Terrorism and Spent Fuel Vulnerability in East Asia Project, published by Nautilus Institute here and here.
[17] This use of the terms cascade and concatenate is borrowed from the climate change impacts literature. Cascade refers to a serial cause and effect across systems. In a complex metasystem of tightly coupled systems, for example, a cascade may mean that the level of activity increases to a threshold or tipping point is reached in one or more subsystems that causes the metasystem itself to transform in structure and state. Concatenation refers to a spatial dimension to cause and effect. Thus, a geographically proximate or downwind effect that leads to an outcome (such as a dam failure leading to flooding downstream) is an example of concatenation. It’s easy to envision such effects in a multi-tier state nuclear threat system before or during a nuclear war.
[18] N. Shinohara, “Nuclear Forensics for Nuclear Security, Present Situation in Japan,” Japan Atomic Energy Agency, presentation International Symposium on Technology Development for Nuclear Nonproliferation and Nuclear Security, February 10, 2016, at: http://www-pub.iaea.org/MTCD/Publications/PDF/SupplementaryMaterials/P1706/Technical_Session_3C.pdf
[19] T. Nichols, “Five Ways a Nuclear War Could Still Happen,” June 16, 2014, at: http://nationalinterest.org/feature/five-ways-nuclear-war-could-still-happen-10665
and P. Brians, “The Causes of Nuclear War,” in Nuclear Holocausts: Atomic War in Fiction, Kent State University Press, 1987 at: https://brians.wsu.edu/2016/11/16/chapter-two/
[20] Robert Ayson, “After a Terrorist Nuclear Attack: Envisaging Catalytic Effects,” Studies in conflict and terrorism, 33:7, 2010, p. 591, at: http://www.tandfonline.com/doi/abs/10.1080/1057610X.2010.483756
IV. NAUTILUS INVITES YOUR RESPONSE
The Nautilus Asia Peace and Security Network invites your responses to this report. Please send responses to: nautilus@nautilus.org. Responses will be considered for redistribution to the network only if they include the author’s name, affiliation, and explicit consent



One thought on “NON-STATE TERRORISM AND INADVERTENT NUCLEAR WAR”