Daily Report Archives
Established in December 1993, the Nautilus Institute’s *N*ortheast *A*sia *P*eace and *S*ecurity *N*etwork (NAPSNet) Daily Report served thousands of readers in more than forty countries, including policy makers, diplomats, aid organizations, scholars, donors, activists, students, and journalists.
The NAPSNet Daily Report aimed to serve a community of practitioners engaged in solving the complex security and sustainability issues in the region, especially those posed by the DPRK’s nuclear weapons program and the threat of nuclear war in the region. It was distributed by email rom 1993-1997, and went on-line in December 1997, which is when the archive on this site begins. The format at that time can be seen here.
However, for multiple reasons—the rise of instantaneous news services, the evolution of the North Korea and nuclear issues, the increasing demand for specialized and synthetic analysis of these and related issues, and the decline in donor support for NAPSNet—the Institute stopped producing the Daily Report news summary service as of December 17, 2010.
RON MINNICH JUNE 9, 2020 I. INTRODUCTION In this essay, Ron Minnich argues: “We cannot build on a foundation that is compromised at all levels. There is no visibility into the system’s behavior. The existing model assumes perfect software: ‘Trust, but don’t verify.’ We need to start anew, from the gates, and work our […]
Go to the article

PAUL BRACKEN MAY 28, 2020 I. INTRODUCTION In this essay, Paul Bracken argues “in a nuclear world we should be careful about attacking enemy communications because doing so leads to greater risks of uncontrolled escalation. The worst possible situation is the one the United States is now in, that is, to not be […]
Go to the article
NAUTILUS INSTITUTE, STANLEY CENTER FOR PEACE AND SECURITY, AND TECHNOLOGY FOR GLOBAL SECURITY MAY 23 2020 I. INTRODUCTION In this study, the authors describe CATALINK, a novel “hotline” system, to enable secure and verifiable communications between leaders during nuclear crises and other high-stakes scenarios. This unique, resilient system is designed for “radical simplicity” from […]
Go to the article

PETER HAYES JANUARY 21, 2019 I. INTRODUCTION In this essay, Peter Hayes suggests that amid the well-known issues that divide North and South Korea, and the potential pathways to lasting reconciliation, there is a little-known concept shared by both sides that taps deep into the cultural resonances of the peninsula’s geography and ecological biodiversity. […]
Go to the article
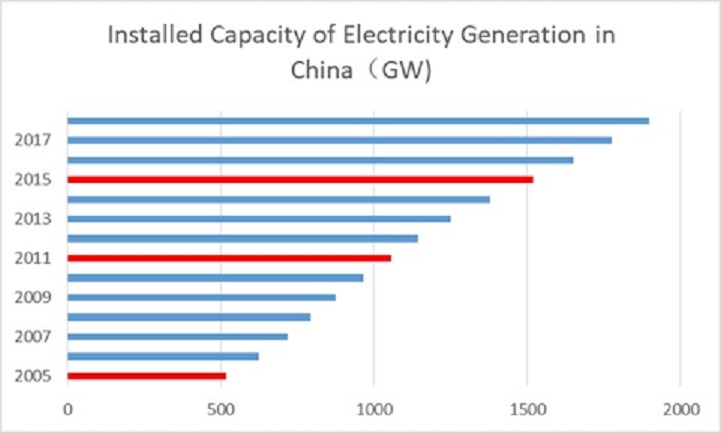
WANG YANJIA, GU ALUN NOVEMBER 24, 2019 I. INTRODUCTION In this Special Report, Wang Yanjia and Gu Alun summarize the status of China’s energy sector and recent trends, and describe projections of China’s energy future in the context of its energy policies. China’s energy imports have been rising in recent years, and environmental, energy […]
Go to the article
JAMES M. ACTON NOVEMBER 21, 2019 I. INTRODUCTION In this essay, James Acton evaluates the risk of inadvertent escalation arising from attacks on dual-use (nuclear and conventional warfare) command, control, communication, and intelligence (C3I) capabilities in a conventional war because such attacks would degrade the target’s nuclear command-and-control system. James Acton is co-director of […]
Go to the article

RON SCHOUTEN NOVEMBER 14, 2019 I. INTRODUCTION In this essay, Ron Schouten examines fundamental concepts of insider threats and provides an overview of the extent and significance of insider threats in US and other NC3 systems. A podcast with Ron Schouten, Peter Hayes, and Philip Reiner on China’s NC3 and emerging technologies is found here. Acknowledgments: […]
Go to the article
CAROL ANN JONES OCTOBER 31, 2019 I. INTRODUCTION In this essay, Carol Ann Jones concludes: “Denying a country use of their nuclear combat forces could be the key to avoiding or limiting damage from a pending strike, but it could trigger unexpected actions from that country’s nuclear forces (assuming the weapons and launch capability were […]
Go to the article

RICHARD TANTER NOVEMBER 2, 2019 I. INTRODUCTION In this essay, the author discusses recently released Australian cabinet papers dealing with a decision in September 1997 to allow the establishment of a Joint Australia-United States Relay Ground Station at Pine Gap to support two United States early warning satellite systems in place of its predecessor, […]
Go to the article

WILLIAM H BOOTHBY OCTOBER 31 2019 I. INTRODUCTION In this essay, Bill Boothby observes: “For all States, there is an obligation to take constant care in nuclear operations to spare civilians and civilian objects. More detailed precautionary rules apply to all States with certain additional rules only applying to States that are party to API […]
Go to the article











