PAUL K. DAVIS
OCTOBER 24, 2019
I. INTRODUCTION
In this essay, Paul Davis suggest that US NC3 modernization “should place increased emphasis on assuring control, avoiding accidents, and avoiding ill-informed or unwise employment of nuclear weapons.”
Paul K. Davis is a senior principal researcher, retired adjunct (RAND). Dr. Davis was a senior executive in the Office of the Secretary of Defense before joining RAND.
A podcast with Paul Davis, Peter Hayes, and Philip Reiner on NC3 goals is found here.
Acknowledgments: The workshop was funded by the John D. and Catherine T. MacArthur Foundation.
This report is published simultaneously here by Nautilus Institute and here by Technology for Global Security and is published under a 4.0 International Creative Commons License the terms of which are found here.
Updated November 12, 2019
The views expressed in this report do not necessarily reflect the official policy or position of the Nautilus Institute. Readers should note that Nautilus seeks a diversity of views and opinions on significant topics in order to identify common ground.
Banner image is by Lauren Hostetter of Heyhoss Design
II. NAPSNET SPECIAL REPORT BY PAUL K. DAVIS
WHAT DO WE WANT FROM THE NUCLEAR COMMAND AND CONTROL SYSTEM?
OCTOBER 24, 2019
Summary
In this paper I take a step back to ask afresh in the year 2019 what we should demand of nuclear command and control and what priorities we should establish when tensions exist among objectives. The answers are different now than in the Cold War, and we should take positive measures not to propagate or resurrect dangerous features that were considered necessary in that earlier period. Nuclear weapons remain distressingly relevant. After years of neglect, there are compelling reasons for recapitalizing and selectively modernizing both the weapons and their command and control systems. As the United States does so, however, it should place increased emphasis on assuring control, avoiding accidents, and avoiding ill-informed or unwise employment of nuclear weapons. That shift of emphasis would be consistent with the trend of nuclear policy for decades, but vestigial mindsets and procedures are still problematic and resistant to change—probably more so than is generally recognized. Desirable changes will come about more readily if the functions and imperatives of nuclear command and control are routinely presented and taught with 21st century sensibilities.
Introduction
I was asked to write a short paper conceptualizing desirable attributes of nuclear command, control, and communications. In doing so I have necessarily omitted much of what is ordinarily front and center in such discussions. In particular, I do not address the myriad of structural and technical issues associated with modernizing the system’s personnel, procedures, facilities, equipment, and communications. Instead, I ask what core functionality should be demanded and how those demands should differ from those of the Cold War. Doing so raises provocative issues of which readers may disagree.
The paper proceeds as follows. After some background largely pointing to Cold War literature on nuclear command and control (Section 2), Section 3 presents a functional model and points out what appear to be important differences between Cold War priorities and those suitable today. In Section 4, I draw conclusions.
Background
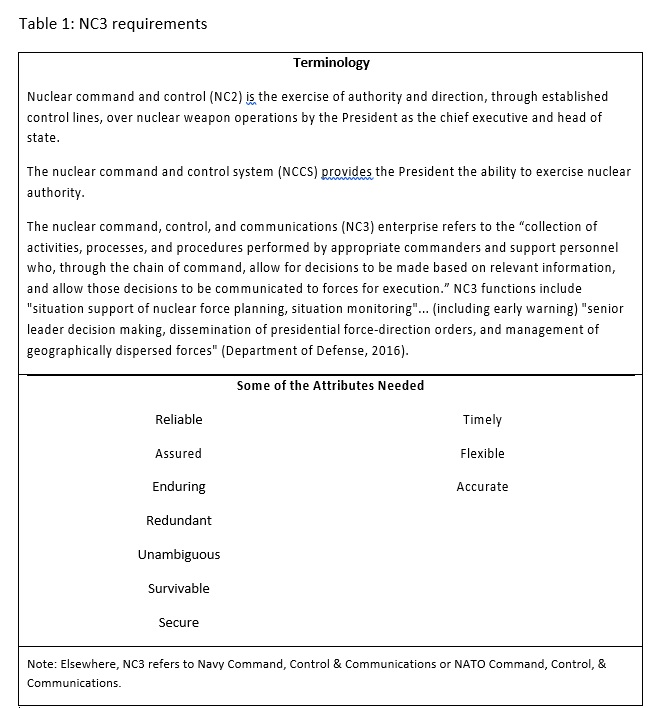
Terminology
The terminology associated with command and control issues is confusing. Table 1 distinguishes among nuclear command and control (NC2), the nuclear command and control system (NCCS), and the nuclear command, control, and communication system (NC3) that DoD operates through its NC3 enterprise to implement the NC2 functions. Table 1 also lists many of the attributes traditionally demanded of NC3 (Department of Defense, 2016).
Background Literature
A significant literature exists from the Cold War regarding nuclear command and control (NC2). Although NC2 and NC3 were shrouded in secrecy, an early book by Paul Bracken addressed credibly many of the most fundamental issues and described apparent characteristics of actual NC2 (Bracken, 1983). Bruce Blair highlighted vulnerability problems related to early warning systems, command procedures, and security (Blair, 1985). The next major contribution was the large and detailed edited book (Carter, 1987) on managing nuclear forces. Soon thereafter, the lead author, Ashton Carter (later the Secretary of Defense), published a good overview for a broad audience (Carter, 1987). Although disagreements existed, the most credible assessment in the mid-1980s was that the NC3 system would assure massive, devastating retaliation in the event of a Soviet first strike (Carter, 1985, p. 605 ff).
That said, the coherence and effectiveness of retaliatory attack might be degraded, especially if the Soviet attack achieved operational surprise with U.S. forces not on full alert. The reader should pause and ponder about the plausibility of that even during the Cold War.[1]
Despite such analyses concluding that retaliation capability was indeed assured, the worry always existed that, in the event of extreme crisis, military authorities would tell the President that (1) launch under attack was necessary if the Soviets began a major attack and that (2) preemption was crucial for national survival in the event that Soviet attack was imminent. The argument for the first of these was that no one could be certain that NC3 would not be paralyzed from an attack and that, even if was sufficiently functional to conduct a retaliatory attack, the attack would be much less effective. The argument for the second claim was simple: there must be military advantage in going first rather than second. The post-exchange balance of forces would favor the side going first and might allow coercion and forced surrender of the other. A speculative variant imagined the hushed hallway conversation, “Mr. President, no one knows what will happen, but the only chance for meaningful national survival (even if not a strong chance) would be if we attack preemptively. Given our intelligence, we might get lucky and paralyze their command and control while destroying most of their nuclear offensive forces.”[2]
The NC3 system did not fare well after the Cold War. The equipment became obsolete due to a lack of new investment. Questions arose about “degradation of authority, standards of excellence, and technical competence.” Embarrassing blunders caused Secretary of Defense Robert Gates to sack the Air Force Chief of Staff and the Secretary of the Air Force (Shanker, 2008). DoD created a task force chaired by James Schlesinger to review nuclear management (Schlesinger et al., 2008a; Schlesinger et al., 2008b). The Air Force reorganized to reinvigorate the nuclear enterprise and related efforts continue (Air Force, 2014; Air Force, 2015). Beginning in the latter years of the Obama Administration, a trillion-dollar effort was begun to modernize U.S. nuclear forces and NC3 over 30 years (Congressional Budget Office, 2017). This reflected a rare bipartisan agreement after years of dispute. It was also contrary to what might have been expected given the administration’s incoming emphasis on deemphasizing nuclear weapons and moving toward their elimination. It was, however, necessitated by the recognition that nuclear strategy and nuclear weapons remained important (Roberts, 2015) and that U.S. capabilities had badly degraded.
Rethinking Functional Requirements
Obviously, much has changed since the Cold War. The changes in the strategic situation include multipolarity, the rise of additional nuclear powers (North Korea, Pakistan, India), the reemergence of Russia as a security problem, and the potential for nuclear crisis to involve more than two parties (Perry and Schlesinger, 2009; Bracken, 2012; National Research Council, 2014; Roberts, 2015). Further, the potential of cyberattacks is now ominous, with consequences for crisis stability among other matters (Cimbala, 2018b). To make things worse, NC3 now depends increasingly on integrated systems and software that are too complex ever to be fully verified. Many accidents may just be waiting to happen (Hayes, 2018a).
I was struck in writing this paper by how differently the NC2 requirements might be framed now, relative to when I was a DoD nuclear analyst in the Cold War. It is not so much that new issues exist (although some do), but rather that the relative importance of issues and cases has changed. This point is sometimes lost in discussions about the decrepit state of infrastructure, the high costs of modernization, cyber threats, and controversial matters such as whether the United States should be developing new weapons, including new low-yield weapons.
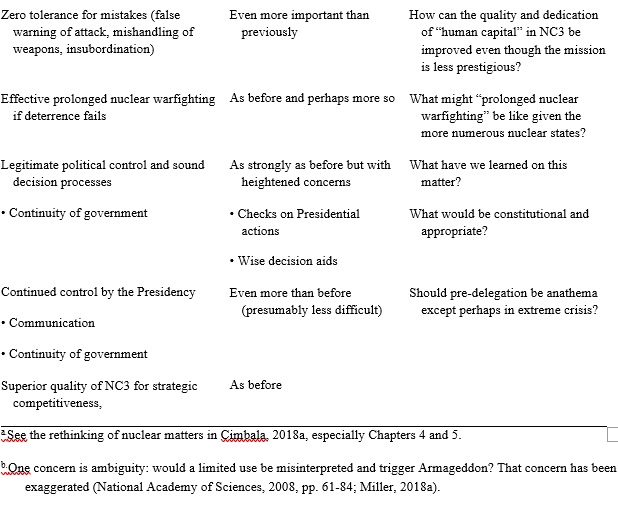 Table 2 is my attempt to show some contrasts. It describes the high-priority requirements during the Cold War in the first column and my sense of what related requirements would look like today in the second column. The third column poses some questions.[3] Table 2 reflects my own review of Cold War strategic thinking (Davis et al., 2016, pp. 2-14). It includes as objectives the always-controversial objectives associated with limited war, prolonged war, and long-term strategic competition. See also Chapter 2 of National Research Council, 2014.
Table 2 is my attempt to show some contrasts. It describes the high-priority requirements during the Cold War in the first column and my sense of what related requirements would look like today in the second column. The third column poses some questions.[3] Table 2 reflects my own review of Cold War strategic thinking (Davis et al., 2016, pp. 2-14). It includes as objectives the always-controversial objectives associated with limited war, prolonged war, and long-term strategic competition. See also Chapter 2 of National Research Council, 2014.
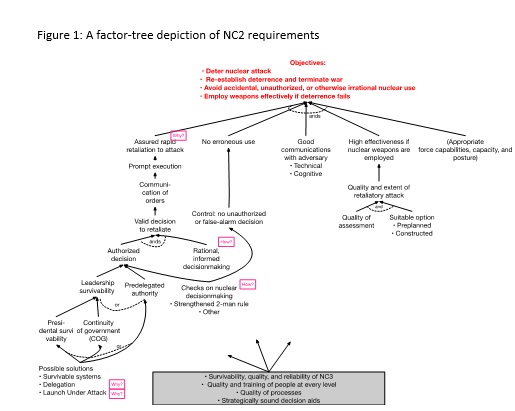
Figure 1 shows a related factor-tree depiction of issues.[4] Objectives are shown at the top and an approximate hierarchy of factors contributing to achieving the objectives are shown below. The first tier of factors decomposes the objectives. The factors are connected by “ands” because the objective is to achieve all of them—to include employing nuclear weapons effectively if deterrence fails. Toward the lower left, Figure 1 indicates that an authorized decision to retaliate could be accomplished by assuring survival of leadership or by pre delegating authority. Assuring survival of leadership long enough to order retaliation might be achieved by riding out an attack or launch-under-attack (LUA). Obtaining an authorized decision, however, is not enough. As indicated by factors to the immediate right, the decision needs to be legitimate, rational, and well informed. Although some of those involved with nuclear strategy and NC3 have been concerned about these issues, most effort on NC3 has gone into engineering capabilities and procedures to implement whatever the President’s decision is. The issue was highlighted in the last days in office of President Nixon—an extraordinary period when Nixon was drinking heavily, sleep-deprived, depressed, and anxious as the Watergate Crisis unfolded (Weiner, 2015).[5]
Conclusions
As characterized as recently as 2016 by the former CIA director Gen. Michael Hayden, the NC3 system for launching U.S. nuclear weapons “is designed for speed and decisiveness. It’s not designed to debate the decision” (Lewis, 2016). Similar points have been made for decades. It has long since been time to re-conceive the system. This paper is a think piece to provoke discussion. With the benefits of a full study and associated facts my own attitudes might change. Nonetheless, I suggest consideration of the following when designing, modernizing, and evaluating NC2 and NC3. Considering them seriously seems appropriate even if (as do I) one opposes further reductions in U.S. strategic nuclear weapons, applauds nuclear modernization, and thinks well overall of the new Nuclear Posture Review (NPR) (Department of Defense, 2018).[6] In any case, my candidates for serious consideration are as follows.[7]
Requirements and Authorities
- Assume that nuclear response after a surprise nuclear use could reasonably be delayed for many hours, allowing for maintaining the presidency’s control through continuity of government measures as necessary and for deliberation. Corollary steps would then be reasonable:
- Banish Launch Under Attack (LUA) postures and procedures except as an option under conditions of extreme alert. Even then, do not allow a LUA posture to be the default.[8]
- Banish pre-delegation of nuclear authority except as an option under high or extreme alert.[9]
- Banish chain pre-delegation of nuclear authority (e.g., through the chain of President, combatant commanded, major subordinate command, to each service’s group commanders) except as an option in ongoing
- Require the President to establish a mechanism to assure that the President cannot authorize first use of nuclear weapons without assent by an independent authority (e.g., Congressional leaders or the Secretary of Defense)[10] unless Congress has already given its assent to [11]
- Use Congressional action and Presidential guidance warning relevant parties to recognize as potentially unlawful (1) any nuclear-use orders inconsistent with standing procedures regarding the conditions of delegation or (2) White House orders issued without evidence of deliberate decision [12]
- Assure that any decision aids are not biased toward a military warfighting [13]
The Personnel System
- Create incentives for some of the best officers to do finite but significant tours responsible for nuclear weapons (and other weapons of mass destruction), and to develop related knowledge, wisdom, and leadership skills (it is doubtful that nuclear-weapon work will again be an attractive full-career field for many top officers).
Standards and Threat Assessments
- Re-establish and enforce the zero-tolerance mindset for nuclear-weapon and NC3 management.
- Deemphasize cost effectiveness and reinstate the importance of redundancy and avoiding common-mode
- In evaluating the certainty of minimum NC3 effectiveness, use independent experts to assure that all threats are considered.
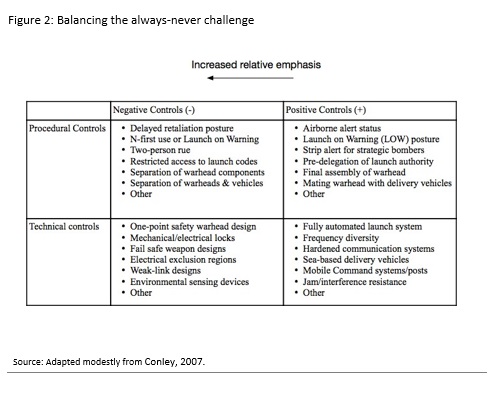
Most of these ideas have been suggested by others over the years, e.g., Senator Sam Nunn (Nunn, 2004) and Bruce Blair (Blair, 2018). A paper by Jerome Conley describes the issues in terms of adjusting the balance between positive and negative controls (Conley, 2007). Figure 2 is adapted from that work (see also Virginia Tech Applied Research Corporation, 2015). Peter Hayes has collected a number of possible norms that might be considered (Hayes, 2018b).
References
Acton, James M. (2018), “Command and Control in the Nuclear Posture Review: Right Problem, Wrong Solution,” War on the Rocks, February.
Air Force, United States (2014), “Air Force Instruction 13-550: Air Force Nuclear Command, Control, and Communications,” Washington, D.C.: Secretary of the Air Force.
——— (2015), “Introduction to Nuclear Operations,” Annex 3-72 Nuclear Operations, Maxwell AFB, Ala.: LeMay Center for Doctrine.
Blair, Bruce (2004), “Keeping Presidents in the Nuclear Dark (Episode #2: the SIOP Option that Wasn’t),” at: https://www.globalzero.org/wp-content/uploads/2019/03/BB_Keeping-Presidents-in-the-Nuclear-Dark-Episode-1-The-Case-of-the-Missing-Permissive-Action-Links_02.11.2004.pdf
Blair, Bruce G. (1985), Strategic Command and Control: Redefining the Nuclear Threat, Washington, D.C.: Brookings Inst.
Blair, Bruce (2018), “Strengthening Checks on Presidential Nuclear Launch Authority,” Arms Control Today, January/February.
Bracken, Paul (1983), The Command and Control of Nuclear Forces, New Haven, Conn.: Yale University Press.
——— (2012), The Second Nuclear Age: Strategy, Danger, and the New Power Politics, New York: Times Books.
Brown, Harold (1981), Annual Report FY 1982, Washington, D.C.: Department of Defense. Burr, William (2012), The 3 A.M. Phone Cal: False Warning of Soviet Missile Attacks,
Briefing Book 371N, National Security Archive, George Washington University.
Butler, George Lee (2016), Uncommon Cause: A Life At Odds With Convention. Volume II: The Transformative Years, Parker, Colorado: Outskirts Press.
Carter, Ashton B. (1985) “Assessing Command System Vulnerability,” in Managing Nuclear Operations, Ashton B. Carter, John D. Steinbruner, and Charles A. Zraket (eds.), 555-610.
——— (eds.) (1987), Managing Nuclear Operations, Washington, D.C.: Brookings. Cimbala, Stephen J. (2018a), Getting Nuclear Weapons Right: Managing Danger & Avoiding
Disaster, Boulder, Col.: Lynne Rienner.
——— (2018b), “Nuclear Crisis Management and Deterrence: Stalked by Cyberwar?,” Cyber, Intelligence, and Security, 29(2), 67-83.
Congressional Budget Office (2017), Approaches for Managing the Costs of U.S. Nuclear Forces, 2017 to 2046, Washington, D.C.: Congressional Budget Office.
Conley, Jerome M (2007) “Nuclear Command and Control in the Twenty-First Century,” in Debating 21st Cemtury Nuclear Issues, Owen C.W. Price, and Jennifer Mackby (eds.), Washington, D.C.: Center for Strategic & International Studies, 226-90.
Davis, Paul K. (1989), Studying First-Strike Stability With Knowledge-Based Models of Human Decision Making, Santa Monica, Calif.: RAND Corporation.
Davis, Paul K. et al. (unpublished), Exploring the Role Nuclear Weapons Could Play in Deterring Russian Threats to the Baltics.
Davis, Paul K. et al. (2016), “Deterrence and Stability for the Korean Peninsula,” Korean Journal of Defense Analyses, 28(1), 1-23.
Davis, Paul K., and Angela O’Mahony (2017), “Representing Qualitative Social Science in Computational Models to Aid Reasoning Under Uncertainty: National Security Examples,” Journal of Defense Modeling and Simulation, 14(1), 1-22.
Department of Defense (2016), 2016 Nuclear Matters Handbook, Washington, D.C.: Office of the Deputy Assistant Secretary of Defense for Nuclear, Chemical, and Biological Programs.
Department of Defense (2018), Nuclear Posture Review, Washington, D.C.: Department of Defense.
Hayes, Peter (2018a), “Nuclear Command-and-Control in the Quantum Era,” as of October 28, 2018, https://nautilus.org/napsnet/nuclear-command-and-control-in-the-quantum-era/
Hayes, Peter (2018b), “Nuclear Command, Control and Communications (NC3): Is There a Ghost in the Machine?,” as of October 29, 2018, https://www.nonproliferation.org/wp-content/uploads/2018/04/180409-nc3-is-there-a-ghost-in-the-machine.pdf
Hirsh, Seymour M. (1983), “The Pardon: Nixon, Ford, Haig, and the Transfer of Power,” The Atlantic, August.
Hoffman, David E. (2009), The Dead Hand: The Untold Story of the Cold War Arms Race and Its Dangerous Legacy, London: Knopf Doubleday.
Lewis, Jeffrey (2016), “Our Nuclear Procedures are Crazier Than Trump,” Foreign Policy, August 5.
McFadden, Robert D. (2014), “James R. Schlesinger, Willful Aide to Three Presidents, is Dead At 85,” New York Times, March 27, A18.
Miller, Frank (2018a), “Addressing Fears about the Nuclear Posture Review and Limited Nuclear Use,” War on the Rocks, February.
Miller, Steven E. (2018b), “Nuclear Battleground: Debating the US 2018 Nuclear Posture Review,” June 5.
Mohr, Charles (1982), “A Scary Debate Over ‘Launch Under Attack’,” New York Times, July 18.
Mulligan, S. P. (2017). Legislation Limiting the President’s Power to Use Nuclear Weapons: Separation of Powers Implications. Washington, D.C.: Congressional Research Service.
Naftali, Timothy (2007), James Schlesinger Interview Transcript, Richard Nixon Oral History Project, Yorba Linda, Calif.: Nixon Library.
National Academy of Sciences (2008), U.S. Conventional Prompt Global Strike Capability: Issues for 2008 and Beyond, Washington, D.C.: National Academies Press.
National Research Council (2014), U.S. Air Force Strategic Deterrence Analytic Capabilities: An Assessment of Methods, Tools, and Approaches for the 21st Century Security Environment, Washington, D.C.: National Academies Press.
Nunn, Sam (2004), “A New Triumph of Sanity,” as of October 28, 2018, https://www.nti.org/newsroom/news/new-triumph-sanity/
Perry, William J., and James Schlesinger (2009), America’s Strategic Posture: the Final Report of the Congressional Commission on the Strategic Posture of the United States, Washington, D.C.: U.S. Institute of Peace.
Roberts, Brad (2015), The Case for U.S. Nuclear Weapons in the 21st Century, Redwood City, Calif.: Stanford University Press.
Rose, Frank A. (2018), Is the 2018 Nuclear Posture Review as Bad as the Critics Claim It Is,
April, Washington, D.C.: Brookings.
Schlesinger, James (Chair) et al. (2008a), “Secretary of Defense Task Force on DoD Nuclear Management, Phase I: The Air Force’s Nuclear Mission.”
——— (2008b), “Secretary of Defense Task Force on DoD Nuclear Management, Phase II.” Shanker, Thom (2008), “2 Leaders Ousted From Air Force in Atomic Errors,” New York Times, A1, June 6.
Steinbruner, John D. (1976), “Beyond Rational Deterrence: the Struggle for New Conceptions,” World Politics, 28(2), 223-45.
Virginia Tech Applied Research Corporation (2015), Nuclear Command, Control, and Stability Framework, Center on Contemporary Conflict Series, Monterey, Calif.: Calhoun Archive (Naval Postgraduate School).
Weiner, Tim (2015), One Man Against the World: The Tragedy of Richard Nixon, New York: Henry Holt and Company.
III. ENDNOTES
[1] Soviet leaders put little stock in a “bolt from the blue” scenario. They were, however, prepared to preempt an imminent U.S. attack (Musgrave Plantation, 1994).
[2] John Steinbruner, sensitive to how people often exhibit non-rational behavior, raised such issues early (Steinbruner, 1976). I confronted some of them, speculating about what, really, might motivate someone to launch (e.g., desperation and a sense of responsibility) (Davis, 1989).
[3] Table 2 reflects my own review of Cold War strategic thinking (Davis et al., 2016, pp. 2-14). It includes as objectives the always-controversial objectives associated with limited war, prolonged war, and long-term strategic competition. See also Chapter 2 of National Research Council, 2014.
[4] Factor trees are simplified versions of influence diagrams (Davis and O’Mahony, 2017). They indicate the approximately hierarchical factors causing an effect at a point in time.
[5] Mr. Schlesinger, as he confirmed years later, became so worried that Nixon was unstable that he instructed the military not to react to White House orders, particularly on nuclear arms, unless cleared by him or Secretary of State Henry A. Kissinger. He reportedly also drew up plans to deploy troops in Washington in the event of any problems with a peaceful presidential succession” (McFadden, 2014; Hirsh, 1983). This report was seemingly contradicted by Schlesinger in an oral interview in which he said that his concern was only assuring proper chain of command and, in particular, protecting against the directives of “hotheaded free-lancers” in the White House (Naftali, 2007, pp. 39-40). It may be that Schlesinger, understanding the constitutional limits of his authority, finessed the matter in his interview. Since he was confident that any troublesome orders would come through Nixon’s national security advisor (i.e., not from Nixon himself), he could rightfully interject himself to assure adherence to the chain of command.
[6] For debate on the NPR, see, e.g., Miller, 2018b; Acton, 2018; Miller, 2018a; Rose, 2018
[7] Longer lists often include admonish not to attack the adversary’s NC3 and to maintain NC3 distinct from that for conventional war. I am skeptical.
[8]LUA was the Cold War operational default, despite policymaker intentions (Blair, 2004; Butler, 2016). Most strategists deplore a LUA posture, although favoring the technical capability. Harold Brown made clear that he did not see LUA as a long-term solution (Brown, 1981, p. 41). Although he lost the debate within the Reagan administration, Under Secretary of Defense for Policy Fred Iklé described LUA as a “hair trigger and irresponsible” (Mohr, 1982). The Soviets had related internal debates and developed a system called “Dead Hand” or “Perimeter” (Hoffman, 2009) that would assure retaliation if the Soviet Union were attacked and its leadership disconnected. Those acquainted with historical false alarms are particularly wary of LUA. On 9 November 1979, National Security Advisor Zbegniew Brzezinski received a 3 a.m. call about the North American Aerospace Command (NORAD) reporting a large-scale Soviet attack. A follow-up call confirmed the attack. That, fortunately, was followed by yet another call declaring a false alarm. Not until 2012 were details released, including admission that the news media had been given false reports underplaying the seriousness with which the warning was taken at the time and the source of error. The claim had been that an airman had inserted the wrong training tape; the truth was that the alarm had been due to a software glitch that apparently could not be reproduced (Burr, 2012).
[9] A variant would allow pre-delegation to SSBN commanders in periods of major tension with peer powers.
[10] Such a precaution would have limitations, since the President could replace the Secretary of Defense.
[11] Many constitutional issues could be resolved with appropriate language, as considered in the “Restricting First Use” bill introduced in Congress during the Obama and Trump administrations to restrict the President’s authority to launch a nuclear first strike (Mulligan, 2017).
[12] Confirming evidence might be, e.g., earlier alert orders or orders with the concurrence of the Secretary of Defense.
[13] Such a biased perspective might focus on the post-exchange ratio of nuclear capability. Better decision aids would also characterize devastation levels, the usefulness of residual force, and sensitivity to assumptions (e.g., how certain is the massive attack said to be imminent or underway?) (Davis, 1989).
IV. NAUTILUS INVITES YOUR RESPONSE
The Nautilus Asia Peace and Security Network invites your responses to this report. Please send responses to: nautilus@nautilus.org. Responses will be considered for redistribution to the network only if they include the author’s name, affiliation, and explicit consent



This is an excellent article brimming with insights. Paul Davis is a leading light on all things nuclear C3I.
My view diverges on only one key point. I do not believe the statement below is correct:
“….the most credible assessment in the mid-1980s was that the NC3 system would assure massive, devastating retaliation in the event of a Soviet first strike (Carter, 1985, p. 605 ff)……”
My own work and operational experience with Minuteman, and with the “Looking Glass” airborne command post (the critical linchpin in the post-attack N3C system), and extensive classified and unclassified research in the late 1970s and 1980s, concluded on the basis of strong evidence that the qualifying point the article then makes is much closer to the actual situation:
“Despite such analyses concluding that retaliation capability was indeed assured, the worry always existed that, in the event of extreme crisis, no one could be certain that NC3 would not be paralyzed from an attack …..”
I would go further and say that strong evidence existed to believe that the likelihood of NC3 paralysis was significant, if not quite high.
The problems that Bruce has written about extensively were real. The more optimistic assessments, however, noted that we had a Triad, each component of which could have delivered massive retaliation. Further, there were somewhat different communication mechanisms for the different components. In some periods, some authorities were predelegated. Finally, an attack coming in period of crisis rather than “out of the blue” would probably have led to special precautions and, in some periods, to authorizing launch under attack. I imagine that these factors all contributed to Ash Carter’s assessment in 1985. All of this said, I–like Bruce–took the second point seriously (i.e., that “no one could be certain…”).
I still would push this question beyond agnosticism. I doubt the Carter assessment rested on primary source materials such as SAC’s series of connectivity studies, MITRE’s tests of TACAMO VLF MEECN range in a jamming environment, DoD’s assessment of EMP effects on “Looking Glass” avionics and communications, etc. My OTA study drew on a raft of these kinds of primary sources to warn of the danger of NC3 paralysis despite the factors (such as pre-delegation) Paul mentions. A study board composed of retired former senior military and security officials agreed.
Hands on involvement in some of the key NC3 assets such as “Looking Glass” also contributed to my gloomy assessment. I recall a state of near panic at SAC in the early 1970s when we learned of an assessment of the possible effects of EMP on this linchpin aircraft’s avionics suggested it might fall out of the sky minutes after exposure. The aircraft’s communications capability was already tenuous (such as the long trailing wire MEECN antenna that frequently jammed during reeling)
The fact that the onboard flag officer had pre-delegated authority was a mitigating but hardly reassuring factor.
I also believe that launch on warning was more feasible on paper than in reality. We practiced it often in ideal conditions and it barely passed the test. In real world circumstances, I strongly doubt it would work against a clever adversary. Major uncertainties included the effects of EMP on the LOW circuitry. Today we add uncertain cyber and ASAT threats to the equation.
There of course is no way short of actual conflict to know for certain how well NC3 would have performed in a nuclear conflict — and even then the outcome would be stochastic with a range of other outcomes just as possible — but all signs pointed then and still point today to gross dysfunction. NC3 always gets short shrift in nuclear modernization programs. Fixing it should be the primary aim of the current program.