PETER HAYES
MARCH 29, 2018
I. INTRODUCTION
In this essay, Peter Hayes concludes: “Given the choices being made by the nuclear armed states to re-embrace nuclear weapons, it is useful to speculate about the potential effects of quantum technology on nuclear forces, and in particular, possible consequences for NC3 systems. At least some of the early intimations of quantum (Q) technology may be superimposed onto nuclear weapons control systems today to anticipate some of the changes already on the horizon.”
Peter Hayes is Director of the Nautilus Institute and Honorary Professor at the Centre for International Security Studies at the University of Sydney. This paper was prepared for the Panel Quantum Control: Of What by Whom and How? ‘QC3I’: Quantum Computing, Control, Communication and Intelligence Symposium, February 17, 2018, Sydney University
Acknowledgment: This report was funded by MacArthur Foundation.
The views expressed in this report do not necessarily reflect the official policy or position of the Nautilus Institute. Readers should note that Nautilus seeks a diversity of views and opinions on significant topics in order to identify common ground.
Banner image: China’s Micius satellite long distance Q communication test from here.
II. NAPSNET BLUE PETER ESSAY BY PETER HAYES
NUCLEAR COMMAND-AND-CONTROL IN THE QUANTUM ERA
MARCH 29, 2018
Quantum physics and derivative technologies may transform the current global security environment bottom-up, working at the atomic level.
Nuclear weapons are devices that work in the other direction, top-down. They are the most powerful weapons controlled by humans; but they are so damaging and so imprecise as to be all but unusable in war except against enemies who have no ability to retaliate in a similar manner.
The entire paradigm of strategic nuclear deterrence is based on manipulating atoms to generate gargantuan amounts of energy in various forms, to inflict massive blast, thermal and radiation effects, onto the mechanical world of classical Newtonian physics—essentially, vaporizing and blowing up instantly populations, cities, military bases and other living and non-living things, and reducing them to smoking, radiating ruins—or threatening to do so.
They work by releasing so much energy and increasing entropy enormously in one place in a few seconds that the resulting explosion is uncontrollable. With exquisite science and astounding technological prowess, these forces have been channeled into different types of nuclear weapons, but the detonation itself is always well beyond human control, often beyond comprehension. The attempt to harness this energy in a controlled manner was displaced into nuclear reactors for the fission process and tokamak containers for fusion reactions, but neither technologies have succeeded in providing controlled energy on a sustainable basis and have proven vulnerable to catastrophic failure. Meanwhile, nuclear weapons abound.
Every time since Nagasaki and Hiroshima that the United States considered using them—in the Korean War, against China in 1958, over Cuba in 1962, in Vietnam in 1966…it found them unnecessary or unusable. No doubt other nuclear weapons states have stood at the edge of the nuclear precipice—Russia and China in 1968, for example, possibly Israel at various times—then backed off.
This potency and disutility gives rise to the imperative to maintain control of these ultimate weapons at all times, leading in turn to a fundamental “always-never” dilemma.
Nuclear weapons must always be controlled, by some combination of organizational and technological control systems, to ensure that they are always available almost instantly for use, to maintain credibility of deterrence aimed at nuclear and non-nuclear armed adversaries, or to reassure allies if you are the United States; and to ensure that they are never used without legitimate authorization and proper authentication, which could lead to inadvertent, unintended, or accidental nuclear attack and reciprocal nuclear war.
Unfortunately, the legacy and brand new command and control systems deployed by nuclear armed states are subject to disruption by new technologies, some of which are near term. Potentially one of most potent of these is quantum technology.
THE EVOLUTION OF AMERICAN NUCLEAR COMMAND AND CONTROL SYSTEMS
Nuclear armed states have built nuclear command and control systems that are supported by communications to and from command centers, computers, intelligence systems, reconnaissance and surveillance systems, and these days, cyberwarfare systems (under the Tallin cyber rules, cyber support systems that play roles in nuclear weapons operations are part of a nuclear weapons system).
The US began with a relatively simple radio-bomber based global nuclear command, control and communications (NC3) system after WWII.
 The United States quickly developed in the sixties a triad of three nuclear forces, relying on land-based missiles, short and long-range bombers, and submarines.
The United States quickly developed in the sixties a triad of three nuclear forces, relying on land-based missiles, short and long-range bombers, and submarines.

Each of these legs of the triad has its own NC3 systems, almost separate from each other, and not inter-operable. 
These systems will send nuclear fire orders to delivery platforms after fusion centers combine intelligence information, monitor targets and adversary nuclear and other forces, assess damage from nuclear strikes, and…if one is lucky, terminate nuclear wars that might break out before, goes the logic, cycles of nuclear deterrence, compellence, and reassurance re-emerge while the world recovers from nuclear war.
In the missiles, old bombers, and submarines, legacy technology, some of it analog such as ancient 8 inch floppy disks, was and still is used today to support targeting of weapons. 
By the 2nd Cold War, the 1980s, the NC3 system “matured” and began to digitize.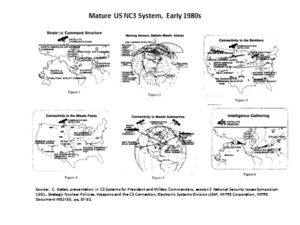
Many of these communication systems are now fully digitized, and are shared with conventional forces and weapons systems in which the nuclear triad is now nested.
This integration of nuclear and conventional C3I along with the forces themselves since the end of the Cold War results in a new tension alongside managing the always-never paradox of nuclear control. That is that US conventional forces strive for C3I systems that push “Power to the Edge” and are characterized by agility, devolution, co-evolution, adaptation, and individual initiative by soldiers, units and entire, networked force structures—the antithesis of NC3I and force structure.
A currently critical issue is whether the new digital information systems, for example, on communication satellites, can provide the bandwidth to support the information requirements of US commanders, especially the President and his coterie, if they are airborne before or during a nuclear war. Like Windows, the sheer size and complexity of the code that runs the most advanced satellite links for example, may generate disabling errors faster than they can be fixed.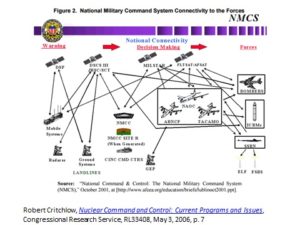
How brittle the triadic NC3 system is to attack, EMP effects, and loss of critical nodes, remains unclear. The system is likely resilient enough to get orders out to attack or retaliate under almost any circumstance; but may not survive to control on-going nuclear operations, nor suffice to terminate nuclear warfighting.
Overall, American NCD, as Defense Information Systems Agency puts it, “is a patchwork of disparate systems, each with its own characteristics. There is no one operating system or coding language.”
Moreover, the role of NC3 systems as an independent source of risk of inadvertent war is unclear. Americans like to think that any increase in NC3 capability is “stabilizing,” that is, should be welcomed by an adversary as stabilizing the balance of terror by giving them confidence that the US will always be able to control its weapons, reducing the propensity of any adversary to fear nuclear attack from weapons that have lost control and are used without proper authority while reinforcing the US ability to use nuclear weapons, thereby reinforcing the credibility of deterrent threats.
Conversely, Americans also think of upgraded NC3 systems as force multipliers—more NC3 capacity can actually increase the delivered nuclear firepower and even substitute for it—an argument advanced at the end of the Cold War as budget reductions forced hard choices on the US military and tradeoffs between nuclear and conventional forces. Of course, a US force multiplier represents increased threat to an adversary, which may then respond in many ways to overwhelm this NC3-based increase in American nuclear fire-power, not just by symmetrical upgrades in its own NC3 and related decision support systems.
The control imperative leads directly to large-scale organizational systems dedicated to political-bureaucratic direction of human behavior, informed by traditional military theory of command-and-control, or by essentially Weberian notions of organizational performance. In the modern era, we have come to expect that such organizations built around complex, high technology may work for a long time at high levels of excellence, but then fail catastrophically in what are called “normal” accidents; and that it is often the tacit knowledge that maintains many of these organizations, not the rigid, stringent standard operating procedures and control systems, such as personnel reliability programs, etc.
Today’s condition of complexity in which nine states now operate nuclear forces with their related NC3 systems gives rise to the interaction of more than 2 nuclear weapons states at a time. In Northeast Asia, for example, at least four nuclear-armed states are party to the Korean conflict. Thus, the impact of Q tech on what may be termed the NC3 bias of these states as they interact, shifting them from primary emphasis on negative rather than positive control, and combining as many technical and organizational control measures as possible to strengthen positive and negative control, may be highly a-symmetric, and consequently highly destabilizing (that is, may induce a threatened party to escalate first to nuclear use to limit their own damage from a nuclear strike, or to win a nuclear war). How this might play out in relation to North Korea is shown below (in this instance, a nuclear terrorist incident starts the ball rolling).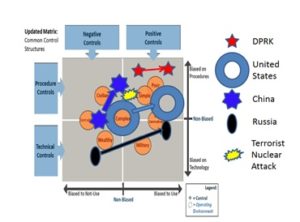
POSSIBLE IMPACTS OF QUANTUM TECHNOLOGIES ON NC3
Given the choices being made by the nuclear armed states to re-embrace nuclear weapons, it is useful to speculate about the potential effects of quantum (Q) technology on nuclear forces, and in particular, possible consequences for NC3 systems. At least some of the early intimations of Q technology effects may be superimposed onto nuclear weapons control systems today to anticipate some of the changes already on the horizon.[1]
These guesstimates are made ceteris paribus, whereas in reality, everything else will be changing at the same time, and Q technology will arrive alongside and will interact with other potent technologies (such as artificial technology and autonomous drones) that will also affect NC3.
Q-communications impact on NC3: The impact of Q technology on communications may disrupt massively the system of authenticating codes that states use to control nuclear weapons and to communicate nuclear fire orders over a variety of physical media—cables, radio transmission, etc. Not only the United States, but also the other eight nuclear armed states, face this apparently relatively near-term threat to the security of their nuclear weapons-related communication systems and code-based control technologies such as permissive action links. Quantum-armed superpowers may be able to reconstruct their NC3 using long distance entanglement effects[2] combined with quantum encryption; but it’s not clear that the less capable nuclear-armed states can sustain the security of their nuclear communications and other decision-support systems against external intrusion, decoding, and demolition or disruption.
Solving Computationally Massive Problems: The ability of quantum computing to tackle anew intractable problems such as determining efficient routes to attack or bypass air defense for nuclear-armed cruise missiles or bombers flying into a heavily defended region such as China’s eastern coastline or North Korea.[3] Likewise, using quantum-enabled navigation systems to operate in war zones where satellite-GPS has been disabled or more likely, heavily jammed by an adversary, may affect the threshold at which nuclear weapons come into play (earlier for a state attacked by an external force using such navigational systems, later for a state able to delay escalation to nuclear brute force by using such navigational systems to make conventional forces more capable against air defenses it is attacking).
Rendering Visible Nuclear Weapons and Delivery Systems—and Command Centers: Quantum clocks and sensing technology may increase transparency of nuclear weapons and nuclear weapons delivery systems, overcoming stealth delivery,[4] and enabling states to identify and track otherwise invisible delivery platforms such as submerged submarines and nuclear armed drones, or of subterranean command centers and missile launch sites used by China and North Korea. With these sites rendered transparent, NC3 systems may be forced to adjust not just to the direct threat of external access to these systems, but to further reduction of the already compressed decision space from minutes to seconds, with the implication that artificial intelligence systems may substitute for humans whose brains are too slow and limited to process sensed information communicated to the nuclear command and control sensors.
Given these trends, nuclear-armed states may be wise to seek to secure widespread concurrence from all states with new norms against attacking the leadership of nuclear armed states, just as the United States and the former Soviet Union (now Russia) are committed by strategic arms treaties to not attack each other’s “national technical means.” Such Q-sensors may also enable nuclear armed states to map with much greater precision the magnetic anomalies of Earth and thereby adjust slightly the intended trajectory of long-range missiles fired over full range (mostly North-South over the pole) rather than in short-range test mode (mostly East-West), thereby increasing the probability of destroying targets. Such a development could increase first strike capability on the one hand and destabilize deterrence on the one hand; or increase the credibility of threats of nuclear attack, thereby reducing the propensity of nuclear adversaries to risk a first strike. The net effects are unknown at this stage and are purely speculative—but may emerge over the time frames in which nuclear modernization of major nuclear weapons delivery platforms will take place.
Supplanting Nuclear and Much Conventional Weaponry: More fundamentally, quantum driven advances in precision of delivery of chemical and physical processes are likely to lead to completely new types of weapon systems that render nuclear weapons even more useless for warfighting than they are today, increasing the opportunity cost that they impose on conventional militaries that actually want to fight wars unencumbered by nuclear weapons or threat of nuclear attack. Such systems are likely to be diffuse, distributed, and work like precision-guided swarms, enveloping fog, or needlelike accuracy against specifically targeted humans or soldiers, or body parts and chemical processes thereof, rather than against large formations or populations.
Thus, Q tech may render not only nuclear but many conventional military systems obsolete and vulnerable to attack. It’s also unclear how nuclear weapons could be used to deter such attacks, which may be extremely agile, swift, and of unknown origin.
In response, some nuclear armed states may increase their reliance on primitive nuclear threat to offset their deteriorating conventional military power although it seems more likely that technologically capable states able to produce and field nuclear weapons would also seek to acquire the new disruptive technologies and combine them in ways that complement each other.
Quantum Balance of Terror? Even more interesting, if quantum weapons began to supplant nuclear and high-end conventional weapons, is what a quantum-based balance of terror might look like? Is a balance even possible in a world that is increasingly endowed with Q technology and possibly many “Q powers?” Is stability or a hegemonic power even possible in such circumstances? And what Q-enabled NC3 would support such a threat system?
And we haven’t addressed yet how cities, non-state actors, and corporations may weaponize Q-technology and thereby affect the operation of nuclear communications and controls when Q technology starts to come into play.
Quantum Monitoring and Verification? We already face the challenge the social media storms may trigger the early warning systems of nuclear armed states.[5] One antidote is to create an independent, impartial early warning fusion center that relies on distributed sensors and indexes of the status of nuclear forces. Q-communications might provide a new way to assure nuclear-armed states that the advice provided by an independent early warning center has not been spoofed by an adversary or malevolent actor, solving the zero knowledge problem[6] addressed in other nuclear arms control and monitoring contexts.
Thus, Q-tech might increase the stability of nuclear conflicts, at least in the short term. It is timely to start exploring what Q-diplomacy might look like.[7]
III. ENDNOTES
[1] M. Biercuk, R. Fontaine, “The Leap Into Quantum Technology: A Primer For National Security Professionals,” War On The Rocks, November 17, 2017, at: https://warontherocks.com/2017/11/leap-quantum-technology-primer-national-security-professionals/
[2] G. Popkin, “China’s quantum satellite achieves ‘spooky action’ at record distance,” June 15, 2017, at: http://www.sciencemag.org/news/2017/06/china-s-quantum-satellite-achieves-spooky-action-record-distance and J. Qui, “Quantum communications leap out of the lab, China begins work on super-secure network as ‘real-world’ trial successfully sends quantum keys and data,” Nature, April 23, 2014, at: https://www.nature.com/news/quantum-communications-leap-out-of-the-lab-1.15093
[3] This is not to suggest that quantum computers can solve the Travelling Salesman problem as suggested in much “Q hype.” However, massive computational power may enable more efficient partial solutions to be obtained for such problems.
[4] S. Chen, “Could ghost imaging spy satellite be a game changer for Chinese military? Scientists are developing a probe to track stealth bombers at night,” South China Morning Post, November 26, 2017, at:
http://www.scmp.com/news/china/society/article/2121479/could-ghost-imaging-spy-satellite-be-game-changer-chinese 66
[5] Peter Hayes, “Reducing The Risk That Social Media Storms Trigger Nuclear War: Issues And Antidotes”, Blue Peter NAPSNet, February 01, 2018, https://nautilus.org/napsnet/reducing-the-risk-that-social-media-storms-trigger-nuclear-war-issues-and-antidotes/
[6] A. Glaser, B. Barak, R. J. Goldston, “A New Approach to Nuclear Warhead Verification Using a Zero-Knowledge Protocol,” 53rd Annual INMM Meeting, Institute of Nuclear Materials Management, July 15–19, 2012, Orlando, Florida, at: http://www.princeton.edu/~aglaser/PU104-Philippe-Barak-Glaser-2015.pdf
[7] R. Mank, “Quantum Diplomacy for a New Technological Age,” Canadian Global Affairs Institute, December 2017, at: http://www.cgai.ca/quantum_diplomacy_for_a_new_technological_age
IV. NAUTILUS INVITES YOUR RESPONSE
The Nautilus Asia Peace and Security Network invites your responses to this report. Please send responses to: nautilus@nautilus.org. Responses will be considered for redistribution to the network only if they include the author’s name, affiliation, and explicit consent.


