GARY A. ACKERMAN
AUGUST 29, 2019
I. INTRODUCTION
In this essay, Gary Ackerman introduces how violent non-state actors (VSNAs) may approach the command and control of nuclear weapons. He suggests that understanding the complexity presented by VNSA NC3 entails considering “traditional concepts of state NC3 (such as the always/never dilemma) and dynamics that are unique to non-state actors driven by a variety of goals and confronting a different set of constraints from those of states.” He concludes that: “it is possible to derive preliminary indications of likely NC3 postures on the part of VNSAs.”
Gary Ackerman is an associate professor in the College of Homeland Security, Emergency Preparedness and Cybersecurity of the University at Albany.
Acknowledgments: The workshop was funded by the John D. and Catherine T. MacArthur Foundation.
This report is published simultaneously here by Technology for Global Security and here by Nautilus Institute and is published under a 4.0 International Creative Commons License the terms of which are found here.
The views expressed in this report do not necessarily reflect the official policy or position of the Nautilus Institute. Readers should note that Nautilus seeks a diversity of views and opinions on significant topics in order to identify common ground.
Banner image is by Lauren Hostetter of Heyhoss Design
NAPSNET SPECIAL REPORT BY GARY A. ACKERMAN
THE NON-STATE DIMENSION OF NUCLEAR COMMAND, CONTROL AND COMMUNICATIONS
AUGUST 29, 2019
Summary
The Nuclear Command, Control and Communications (NC3) of violent non-state actors (VNSAs) is a topic that has received very little prior attention, but is one that demands careful consideration. On the one hand, the amorphous and obtuse ideologies of some VNSAs and a talent for conducting clandestine activities among many VNSAs complicate traditional notions of NC3, especially since most VNSAs do not seek a stable nuclear standoff akin to the MAD years of the Cold War. On the other hand, by combining some inherent aspects of organizational dynamics and state-level NC3 with what we know of VNSA behavior, it is possible to derive preliminary indications of likely NC3 postures on the part of VNSAs. This brief paper will introduce the complexities surrounding VNSA NC3, arguing that an adequate understanding of the issues involved requires consideration of both traditional concepts of state NC3 (such as the always/never dilemma) and dynamics that are unique to non-state actors driven by a variety of goals and confronting a different set of constraints from those of states.
Introduction[1]
Imagine, if you will, a scenario in which the President of the United States is working in the Oval Office early one morning when the Secretary of Defense and the National Security Advisor burst in to inform her that their worst fears have been realized—a faction of the Tehreek-e-Taliban Pakstan has acquired three viable nuclear weapons from Pakistan’s stockpile within the past 72 hours. In addition to the obvious step of immediately placing all intelligence and nuclear detection assets on full alert, the President asks for response options. The Secretary of Defense declares that they know with high certainty the approximate location of the faction’s leadership, and that an overwhelming strike could decapitate the group and perhaps, if the weapons are collocated with the leaders, destroy the weapons as well. The National Security Advisor, a man known for his perceptiveness, protests, “Ms. President, what if the weapons have already been moved out of the area and the leadership has predelegated authority to its operatives to detonate the weapons in the event that they are killed? We don’t know yet that they want to use the weapons to immediately attack us — they might want to bargain with us or deter us. If we preemptively wipe out their leadership, this could precipitate the very catastrophe that we are trying to avoid.” Unfortunately, no-one knows the most likely nuclear command and control disposition of the terrorist group and so the President will be forced to make the gravest of decisions under unenviable levels of uncertainty.
Needless to say, the above scenario paints a sub-optimal policy picture. In such an extreme set of circumstances, having at least some knowledge about the nuclear command, control and communications (NC3) of the particular adversary, or even of non-state actors in general, would be crucial. It is certainly not something that should first be considered during a crisis. This type of understanding would also prove exceedingly valuable in less urgent circumstances, such as setting up the Global Nuclear Detection Architecture to maximize the probability of detecting the movement of non-state nuclear weapons. However, despite more than five decades of examining NC3 in the context of states[2] and four decades considering the possibilities of nuclear terrorism,[3] there has been almost no serious consideration of how violent non-state actors (VNSAs) would employ nuclear weapons if they ever got their hands on them.[4] This condition of strategic ignorance is further complicated by the observation that non-state actors often evolve far more rapidly than states, while themselves operating in a geopolitical, technological and environmental landscape undergoing constant transformation.
This brief paper will introduce the complexities surrounding VNSA NC3, arguing that an adequate understanding of the issues involved requires consideration of both traditional concepts of state NC3 (such as the always/never dilemma) and dynamics that are unique to non-state actors driven by a variety of goals and confronting a different set of constraints from those of states.
VNSA NC3 in Perspective
To a certain degree, all organized entities—be they states, VNSAs, corporations or preschools—face a similar set of constraints and alternatives when it comes to exercising authority at a distance, which in a military context encompasses command, control and communications. The degree of uncertainty under which an actor operates, its core organizational values and goals, the configuration of its decision making and power structures, and levels of distance between decision makers and implementers (including issues of loyalty, trust and competence) are all key issues in this respect.[5] Beyond these basic organizational dynamics, the first place to look for how VNSAs might approach the command and control of nuclear weapons is the history and theory of state NC3, especially given the tremendous amount of attention, from Thomas Schelling and Herman Kahn to more modern theorists, that the topic has received.[6]
The first salient concept that one might borrow from the state experience is the always/never dilemma. The first aspect of this is the idea that if one possesses nuclear weapons, they should always be available for use when needed, or else one’s nuclear weapons strategy (such as being able to credibly retaliate against a first strike to maintain deterrence) will “fail impotent.” The other horn of the dilemma is that nuclear weapons should never be used in an unauthorized manner, which would result in a “fail deadly” condition (with obviously deleterious consequences). The dilemma resides in the observation that measures to ensure the first condition often prejudice the second, and vice versa.
To address this dilemma, states need to make a choice between a more assertive or a more delegative NC3 posture. Without excessively retreading old ground, in a completely assertive posture, leadership retains control of deployment and use decisions, while in a completely delegative posture the leadership gives authority to subordinates (e.g., field commanders) to make deployment and use decisions. In practice, these ideal types rarely if ever manifest and postures are adopted that contain elements of both types, for instance where leadership retains authority to use weapons unless communications with field commanders are severed, in which case authority devolves to the field. Scholars have offered numerous theories for when states adopt a particular posture. Among the more prominent are Peter Feaver’s assertion that when time pressures are high, there is a tendency towards a delegative NC3 posture,[7] while more volatile civil-military relations result in a more assertive posture.[8] Other variables that have been argued to influence the posture include the size, quality and dispersion of the arsenal,[9] the general style of the leadership[10] and the availability of enabling technologies like PALs.[11]
While they share some basic organizational attributes, VNSAs differ from state entities in several respects. These include their structure, resources, conceptions of victory and so forth. Of particular relevance to NC3 is that, unlike states, VNSAs might not adopt nuclear deterrence as an operating strategic principle, instead favoring kinetic action to achieve their goals, which renders concepts such as a second strike capability moot. In addition, many VNSAs—especially those that lack a terrestrial constituency—might have a very different tolerance for risk or notion of success, where they do not necessarily envisage a “day after” the use of a nuclear weapon or might abide a weapon that fails deadly.
Therefore, although certain of the abovementioned state NC3 dynamics, such as consideration of the leadership’s vulnerability to decapitation and a strong desire to avoid unauthorized detonations, might transfer readily to VNSAs, others might not. It is thus necessary to engage in a closer examination of VNSAs’ motivations and capabilities for pursuing nuclear weapons, as well as how they conduct operations, to understand their NC3 proclivities.
Nuclear VNSAs: Strange Attractors
Although there are a wide variety of VNSAs, including terrorists, insurgents, transnational criminal organizations and misanthropic lone actors,[12] the vast majority do not pose any type of nuclear threat simply because they lack any motivation to acquire nuclear weapons. For most VNSAs, nuclear weapons are overkill insofar as their goals can be served with far less destructive means. Among the few reasons why non-state actors might be drawn specifically to pursue a nuclear capability are as follows:[13]
- An express desire to cause massive numbers of casualties and ghastly levels of destruction.
- To render vital areas uninhabitable and/or critical infrastructure unusable for extended periods of time (area denial).
- To inflict unprecedented levels of psychological impact and social disruption on a target population.
- To bring about an ideological catharsis (e.g., to initiate the end times).
- An idiosyncratic psychological fetish for nuclear weapons.
- To acquire prestige and status commensurate with a “world power” with respect to internal or external audiences and competitors.
- To attempt to asymmetrically and absolutely deter or coerce a much more powerful enemy (especially a state).
At the very least, for a group or individual to seriously consider the use of nuclear weapons, they must evince unwavering indifference to the catastrophic death and destruction wrought by a nuclear detonation. Even amongst the plethora of currently active VNSAs, such maximal goals are rare; nuclear weapons will thus only appeal to a small and very specific proportion of VNSAs. Indeed, there have only been 18 recorded plots (some of which were likely less than completely earnest) of VNSAs pursuing nuclear weapons.[14] And of those to whom such weapons are attractive, an even smaller subset will have any possibility of successfully acquiring a nuclear capability, given the arduous technical, organizational and logistic obstacles involved.
An in-depth qualitative and quantitative study of future non-state nuclear perpetrators[15] revealed that among violent organizations, those espousing a jihadist ideology[16] were ranked as the highest threats. This is not surprising in light of the above motivational stimuli, given that many adherents within this milieu believe they are fighting on behalf of a deity who wants them to cleanse the world of ignorance (jahiliyyah), are engaged in a millenarian conflict with the forces of evil (epitomized by the liberal West) and are justified in seeking revenge for perceived past massacres against the Muslim world. Neither is this affinity purely theoretical; there has been well-documented interest in nuclear weapons on the part of al-Qa’ida and related groups, such as the self-proclaimed Islamic State, from several pronouncements justifying the use of nuclear weapons,[17] to grandiose schemes,[18] and even nascent attempts in the 1990s and early 2000s to acquire fissile material.[19] This interest shows no sign of dissipating, as seen in the recent surveillance of a senior official of the SCK CEN Nuclear Research Center in Belgium, apparently as part of an effort to gain access to nuclear materials.[20]
Following close behind in terms of motivation (although not quite in terms of capability) are modern apocalyptic-millenarian groups along the lines of Aum Shinrikyo, the Japanese doomsday cult who actively pursued nuclear know-how from Russian scientists and likely established an abortive uranium mining effort in Australia in the early 1990s.[21] There has also been steady interest in nuclear weapons on the part of far right extremists in the United States, spurred on by the Turner Diaries, a white supremacist novel that serves as one of the seminal texts for the movement and in which nuclear weapons feature prominently as catalysts for defeating its enemies.[22] One recent manifestation of such interest is the establishment in 2013 of the self-proclaimed Atomwaffen [atomic weapons] Division, a neo-Nazi outfit based in Florida but with membership in several states.[23]
Beyond terrorist or insurgent actors, one threat that appears prominently in various analyses[24] is that of a nuclear insider, an individual with both extensive technical expertise and high levels of access to nuclear weapons or materials. If such an individual were to become sufficiently disgruntled, he or she could use their knowledge to circumvent existing controls and security measures and to steal nuclear materials. Certain analyses also point to highly proficient criminal organizations as posing a non-negligible threat to the security of nuclear materials, which they could then transfer (for pecuniary or other reasons) to extremists willing to use them.[25]
Lest one assume that just because past attempts have failed, that no VNSA will be able to acquire a nuclear capability, it is worth noting that VNSAs have proven themselves to be adept at a variety of complex engineering efforts, from building long-range submersibles to bespoke mortars[26] and large-scale production of conventional[27] and chemical weapons.[28] These demonstrated capabilities are easily equivalent to weaponizing fissile material and might even be sufficiently sophisticated to allow such groups to engage in enrichment. Given that there have been at least 98 recorded cases where high-threat fissile material has fallen out of regulatory control,[29] and multiple prior attacks on facilities housing nuclear weapons or fissile material,[30] this implies that one cannot be too sanguine about the prospects of a determined VNSA acquiring a nascent nuclear arsenal. At the same time, it must be recognized that there is a far lower probability of this particular threat than that of almost any other known threat from such non-state actors.
In the specific context of C3, VNSAs have succeeded in creating and maintaining sophisticated command, control and communications capabilities over large distances at both the operational and strategic levels. For example, Lashkar-e-Taiba attackers succeeded in carrying out twelve coordinated attacks across Mumbai in November 2008, killing over 160 people, all the while maintaining contact and command with handlers in Pakistan over satellite and cell phones.[31] Another example is the creation and maintenance by Los Zetas, a brutal Mexican criminal organization, of an encrypted radio network that ranged over most of Mexico, which was used to coordinate their actions and gain an operational edge over rivals and the government.[32] An even more impressive example of command and control over distance is the practice, according to incarcerated crew members, that if one of the “narco-submarines” operated by the Revolutionary Armed Forces of Colombia (FARC) was about to be interdicted, the captain of the vessel would be required to contact a division leader back in Colombia via satellite communication to receive orders whether to scuttle and/or abandon the submarine.[33] These examples show that for many VNSAs, assertive C3 is a viable option.
As to the general practice of VNSA conventional C3, a study of eight complex attacks by terrorist organizations confirmed that terrorists, at least, utilize a variety of postures.[34] In addition to three cases of delegative C3 and four cases of a more assertive C3 posture, there was a case where the C3 could best be described as “predetermined,” in which operatives were required to follow a prescribed script without the options of either deviating from the preplanned actions or contacting leadership for guidance in response to changes in external circumstances. In this third type of posture, the operatives are essentially acting as preprogrammed automatons following the leadership’s preassigned instructions to the letter, irrespective of unanticipated developments.
Although limited inferences can be drawn from such a small number of case studies, the analysis suggested that “groups with strict hierarchy and adherence to orders from hardline leadership tend to have either pre-determined or assertive command and control, and are unlikely to have a delegative system. In contrast, delegative configurations dominate when leadership perceives omnipresent and existential threats.”[35]
Tectonic Shifts
Nuclear non-state adversaries do not exist in a static context: there are a number of discernible trends, as well as a handful of plausible wild cards, in the global socio-political, natural and technological environment that could increase the non-state nuclear threat in the next decade. While limitations on space preclude an extended discussion of all of these possible shifts, brief illustrative examples are presented to support this claim.
Emerging trends that could facilitate non-state nuclear pursuit include the following:
- Changes in the natural environment (including climate change, desertification, and acidification of the oceans) can have both direct and indirect impacts on the threat. Indirectly, these changes are likely to lead to food shortages and mass migrations, which can exacerbate existing zones of instability and create new ones. These can in turn become breeding grounds for extremism and undermine existing nuclear material security measures. For an example of a more direct impact, it can be observed that as natural sources of fresh water dry up, many countries in already politically unstable parts of the world will be forced to turn to alternative means to supply their populations with drinking water and irrigation. Littoral countries will probably turn to desalination and, given the shortage of power in many developing countries that will be most affected by climate change, nuclear-powered desalination plants might prove to be the best option.[36] While this might be life-saving for the broader population, it also means that nuclear materials and expertise could for the first time move to parts of the world—such as North Africa and the Persian Gulf—where VNSAs tend to flourish.
- Greater geopolitical and economic polarization, exemplified by the rise of China’s military and economic power, a revisionist, autocratic Russia and the United States’ recently truculent trade policy, augur a less cooperative international environment and more displacement of populations.[37] Amid this geopolitical tension, intergovernmental nuclear security and counterterrorism efforts can become more difficult (or cease entirely) and “grey zone” conflicts such as those in Ukraine and northern Syria can become more common. The latter can serve as breeding grounds for extremism, lawlessness, and general insecurity, which can increase both the capacity of VNSAs and the vulnerabilities of materials.
- Jihadist shifts in the wake of the Islamic State. The loss of the territorial caliphate will likely lead to a fracturing of the jihadist milieu. Smaller successor groups, although initially having lower capabilities than the Islamic State, will likely vie with one another to assume the mantle of the jihadist vanguard, thus incentivizing spectacular attacks and a renewed focus on the West as revenge for, in their minds, destroying the Caliphate.[38] At the same time, those factions like the al-Qa’ida franchise, which advocate a more patient build-up of forces and are perhaps more suited to the onerous task of acquiring a nuclear weapons capability, will once again gain prominence within the milieu.
- Fluid, hybrid forms of sovereignty are likely to become more apparent. As the centralized nation-state decreases in importance or capacity in several regions of the world, there are likely to arise increasingly autonomous sub-state entities, potentially including de facto city-states, breakaway regions, multinational corporation-controlled enclaves and even floating artificial countries.[39] While some of these new entities will strive to be responsible international citizens and adopt the existing norms of non-proliferation, others may be unable or unwilling to do so and might functionally operate as permissive entrepôts where anything is available for a price and no-one asks too many questions, in particular about nuclear material movements.
- The democratization of a range of technologies, wherein they become cheaper, more accessible and easier to understand, is likely to empower terrorists and other VNSAs. Some of these technologies, such as additive manufacturing and artificial intelligence, would be directly helpful in the construction of the non-nuclear components of a nuclear weapon, while others, such as cyber-viruses and unmanned vehicles, might facilitate the penetration of secure facilities and the acquisition of weapons-usable material. The flip side of this development is the globalization of education paired with underemployment, where millions of youths in regions like the Middle East will have access to cheap, effective, highly technical training, but then be unable to find a job in corrupt, nepotistic polities. The logical consequence is increasing numbers of increasingly technically proficient, yet disaffected, young people in many countries. This alienated, educated population will be ripe for exploitation by a variety of criminal and extremist VNSAs, which can only serve to bolster these entities’ capabilities.
In addition to these macro-trends, there are a series of potential “wild card” events with low or unknown probabilities that could exacerbate the threat by providing greater opportunities for VNSA nuclear weapons acquisition. Many are in fact specific manifestations of one or more of the above dynamics:
- Severe natural disaster (e.g., hurricane, tsunami or earthquake) that jeopardizes nuclear security in the immediate aftermath of the event and in the longer run diverts resources towards recovery efforts and away from nuclear security and countering VNSAs.
- Failed nuclear state (the ones most often mentioned are Pakistan and North Korea), which results in increased vulnerabilities to opportunistic insiders or VNSAs with respect to the misappropriation of nuclear weapons or materials.
- Reenergized Iranian nuclear enrichment and resulting conflict with Iran that results in nuclear materials falling out of control or the intentional provision by elements of the Iranian regime of weapons-usable material to one or more of Iran’s proxies, such as Lebanese Hizb’allah or the Yemeni Houthis.
- Breakthrough technology, such as small-scale laser enrichment, makes it feasible for VNSAs to produce their own fissile material with a small industrial footprint.
Factors Influencing VNSA NC3
The only previous study of which this author is aware that deals squarely with VNSA NC3 is one where the author and a colleague explored the phenomenon with the aim of building a model to anticipate the likely nuclear command and control postures of terrorist organizations.[40] It sought to rank the relative likelihood of a VNSA adopting an assertive, delegative or predetermined NC3 posture. The study built upon an extensive survey of the extant literature on social and organizational psychology and that on state nuclear command and control, by adding insights gained from a series of case studies (mentioned earlier) of previous cases of terrorist command and control to develop a provisional model. This model was in turn critiqued and further developed through structured and unstructured elicitation during a workshop attended by a variety of experts in organizational psychology, terrorist behavior and state nuclear command and control. The output of the workshop (consisting of over fifty variables) was then refined to create a framework consisting of ten primary factors and a dozen secondary factors. This framework was subsequently applied to six real and hypothetical VNSAs and the results compared with the best qualitative estimates of subject matter experts familiar with those organizations.[41]
The model was designed to apply to terrorists in particular as the most likely nuclear VNSAs, but it should be applicable to other types of VNSA organizations with little to no modification. While the complete model includes rules for scoring, weighting and aggregating the primary and secondary factors, the major effects within the model are summarized below for each of the ten main factors:
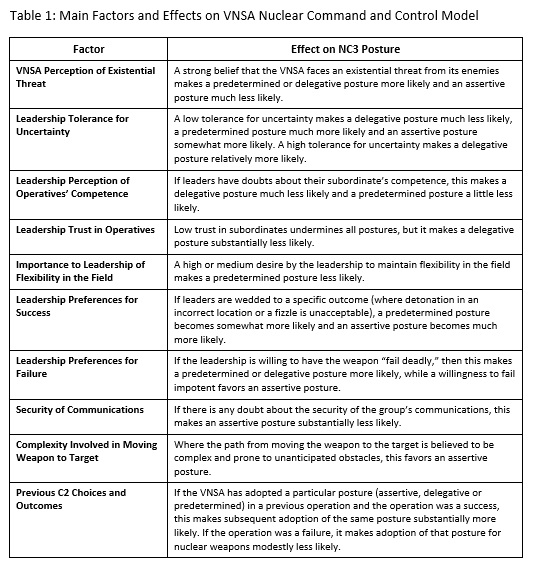
While the precise configuration of factors will vary from VNSA to VNSA, an illustrative example can be offered to demonstrate the operation of the model. Taking an apocalyptic millenarian cult that is a modern analog of Aum Shinrikyo, for instance, the leadership is likely to desire a specific outcome (that aligns with its prophecies), to have lower trust in the loyalty of its operatives and in the security of its communications (due to a common paranoia among leaders in such organizations), but a high estimation of its members’ competence (stemming from a belief in the group’s superiority). It is likely to perceive itself to be facing an existential threat (based on its millenarian outlook) and to be willing for a device to fail deadly (based on its belief in “destroying the world to save it”), while having a low tolerance for uncertainty. Combining the effects of these factors[42] yields an estimate from the model that a predetermined NC3 posture is the most likely outcome. This accords with the independent qualitative estimate provided by the subject matter expert and was incidentally more or less the posture that Aum Shinrikyo used in its most infamous attack when it released the nerve agent sarin on the Tokyo subway in 1995.
Manifestations and Variations of VNSA NC3
The above model on its own is oriented towards scenarios where the ultimate goal of the VNSA is to detonate a nuclear weapon. However, there are other circumstances wherein a VNSA would seek to utilize one or more weapons for deterrent or coercive purposes, with detonation as a sub-optimal outcome. It could manifest in the prepositioning of a nuclear weapon in one or more cities, demonstration of that fact and then seeking to bargain with the VNSA’s adversary in a form of “nuclear hostage-taking.” This might occur, for example, if a less millenarian-inclined jihadist group sought to have foreign troops vacate the Middle East or, conceivably, if a powerful transnational criminal organization wanted to deter states from inhibiting its freedom of action through a key smuggling pathway. However, this type of employment of nuclear weapons is probably more likely among VNSAs (such a putative city-state or irredentist insurgents) who aspire to eventually attain a state-like status or at least some form of traditional sovereignty. In such cases of compellence or deterrence, certain secondary factors already present in the model (such as the VNSA’s assumptions about likely enemy responses and the leadership’s desire for prestige) would become more salient in calculating a likely NC3 posture, for example, by affecting preferences for success or perceptions of existential threat.
Moreover, several new factors, most of them borrowed from concepts of state NC3, would also need to be taken into account. The most important of these are leadership perceptions of both their own and their nuclear weapons’ detectability and vulnerability with respect to the forces of the targeted state and the size and dispersal of the VNSA’s nuclear arsenal. Both of these are linked to a putative “second strike” capability on the part of the VNSA. It is logical to assume that, all of the other factors above being equal, a VNSA with multiple weapons that are dispersed and well-hidden, and whose leaders feel secure against reprisal, would adopt a more assertive posture, while possessing a single weapon and a vulnerable leadership would suggest a more delegative or even predetermined posture.
In addition to these abovementioned factors, the following factors will be central to the success of any attempts at “nuclear hostage taking” of this type:
- The reliability and credibility with which messages can be communicated to the target(s) of the compellence or deterrence, including the extent to which the VNSA can demonstrate its capability;
- The nature of the demands, which cannot have a greater negative utility for the target than the risk of a nuclear detonation; and
- The VNSA’s flexibility in its demands and its leadership’s willingness to negotiate or compromise.
Another aspect to consider is the impact on VNSA NC3 of modern technologies. Besides the developments noted above that might facilitate VNSA acquisition of nuclear weapons in the first place, most of the technological influence on VNSA NC3 will stem from technology’s impact on the security of communications. First, signal spoofing (a tactic used widely by hackers and other cybercriminals) can make it difficult to trace the origin of an electronic message and thereby complicate locating the leadership. Second, a multiplicity of possible communications channels, from social media to in-game chats over online gaming networks, decrease the signal to noise ratio and make it more difficult for security forces to monitor all possible communications between different parts of a VNSA. Some less responsible social media platforms like Telegram allow for encrypted messages which self-destruct, and they are already widely used by nefarious actors. Similarly, social media can allow one-way communications between leadership and field operatives (e.g., by sending out a seemingly innocuous tweet to followers that includes coded instructions on how to proceed). Last, but not least, stronger cryptography or even the advent of theoretically uninterceptable quantum cryptography[43] will enable VNSAs to hide the content of their communications. All of these developments will facilitate an assertive NC3 posture by increasing the leadership’s confidence in being able to maintain secure communications with their operatives.
Possible Countermeasures
Disrupting VNSA NC3 is one means of reducing the threat of nuclear attack from this quarter (along with such measures as enhancing the security of nuclear materials, instituting a Global Nuclear Detection Architecture, increasing preparedness for and response to nuclear attack and degrading VNSA capabilities more generally). However, as indicated in the introductory scenario, how to best disrupt VNSA NC3 depends very much on knowing the type of posture being employed by the VNSA. Options for each posture are as follows:
- Assertive NC3 posture: In this case, there might very well be opportunities to use kinetic measures to decapitate the leadership of the organization and thereby throw the plot into disarray. Another option is to intercept or block communications between the leadership and those in the field. If field operatives with a nuclear weapon have strict orders to await a go signal from leaders before proceeding, preventing this signal from being sent or received might give authorities sufficient time to interdict the perpetrators.
- Predetermined NC3 posture: This case is theoretically the most secure of the NC3 options in that it removes any need for decision making in the field or communicating with superiors. However, it is also the most brittle, since if the predetermined script has not taken a particular eventuality into account, the entire operation might founder for lack of operatives knowing how to proceed. Creating unexpected obstacles (such as random “surges” in nuclear detection asset deployment) might thus serve to disrupt plots under this type of NC3.
- Delegative NC3 posture: This is the hardest case to disrupt NC3 in that the field operatives essentially act as their own decision makers. If they are sufficiently competent and loyal, there is little to be done to disrupt command and control.
Given that an assertive posture is preferable from the point of view of countering VNSA NC3, it is interesting to consider how VNSAs could be manipulated into adopting this posture. Some initial suggestions might be to use psychological operations that undermine leaders’ confidence in their subordinate’s competence or make it appear as if certain communications channels are secure (thus encouraging leaders to adopt an assertive posture and utilize those channels), while actually being able to compromise those channels.
Last, there is the question of the role that international law can play in confounding VNSA NC3. While there are a variety of international legal instruments devoted to preventing non-state actor nuclear acquisition, including UN SCR 1540, the International Convention for the Suppression of Nuclear Terrorism, the Convention on Physical Protection of Nuclear Material Amendment and the Proliferation Security Initiative, none of these is specifically geared towards disrupting or influencing VNSA NC3. To the extent that these legal regimes frustrate the acquisition and movement of nuclear materials and enhance general international counterterrorism and anticrime collaboration, they can go some way towards complicating VNSA NC3 by affecting one or more of the factors in the model above.
Perhaps a specific legal instrument or regime that is focused on actions by states after a VNSA obtains a weapon might provide additional leverage. For example, preauthorization of overflight rights in the event of a credible VNSA acquisition of a nuclear weapon might be useful, or an instrument that makes it legally binding for a state that discovers that a VNSA has successfully acquired a nuclear weapon to share this information immediately with all signatories. However, some of these measures might paradoxically make an assertive posture (the most desirable in terms of leveraging VNSA NC3 by security forces) less likely. For example, legal measures that give states more leeway to engage in kinetic operations against terrorist bases in other states might increase the VNSA’s sense of existential threat and make a delegative posture more likely. This does not mean that such measures should not be implemented, but it indicates that international legal measures can have different impacts on different elements of the VNSA nuclear threat.
Conclusion
VNSA NC3 is a topic that has received very little prior attention, but is one that arguably demands careful consideration. On the one hand, the amorphous and obtuse ideologies of some VNSAs and a talent for conducting clandestine activities among many VNSAs complicate traditional notions of NC3, especially since most VNSAs do not seek a stable nuclear standoff akin to the MAD years of the Cold War. On the other hand, by combining some inherent aspects of organizational dynamics and state-level NC3 with what we know of VNSA behavior, it is possible to derive preliminary indications of likely NC3 postures on the part of VNSAs. Since there are no indications that the threat of VNSA nuclear weapon acquisition will diminish any time soon, it is incumbent upon the global security community to explore this area more deeply and to adopt forward-leaning policies and procedures for divining and confounding VNSA NC3 postures well before a nuclear crisis arises.
III. ENDNOTES
[1] The author would like to acknowledge the contributions of Charles Blair, then of the Federation of American Scientists, with whom he collaborated on developing the model described in this paper and who was responsible in the original study for much of the background research on NC3.
[2] Several early treatises on nuclear strategy contained elements of NC3, including Bernard Brodie, Strategy in the Missile Age (Santa Monica: RAND, 1959); Thomas C. Schelling. The Strategy of Conflict (Cambridge, MA: Harvard University Press, 1960); and Herman Kahn, On Thermonuclear War (Princeton, New Jersey: Princeton University Press, 1960).
[3] For early discussions, see Brian Michael Jenkins, The Potential for Nuclear Terrorism (Santa Monica: RAND Corporation, 1977); and Paul Leventhal and Yonah Alexander (eds.) Preventing Nuclear Terrorism (Lexington, MA: D. C. Heath, 1987).
[4] Almost all of the discussion has focused on the likelihood of acquisition, often based on the formula of Threat = Motivation x Capability, with assumptions often made—with little detail offered—that there will be automatic deployment or use of a nuclear weapon by a VNSA if it ever succeeded in obtaining one.
[5] Among the more seminal social and organizational works relevant to this area are: John P. Kotter, Organizational Dynamics: Diagnosis and Intervention (Reading: Addison-Wesley, 1978); Edgar H. Schein, Organizational Psychology, 3rd ed. (Englewood Cliffs, NJ: Prentice-Hall, Inc., 1980); Henry Mintzberg, “Structure in 5‘s: A Synthesis of the Research on Organizational Design,” Management Science, Vol. 26, No. 3 (1980); Susan Wright, “Culture in Anthropology and Organizational Studies,” in Susan Wright, ed., Anthropology of Organizations (New York: Routledge, 1994); and Geert Hofstede, Culture and Organizations: Software of the Mind (London: McGraw-Hill, 1991).
[6] Some of the more prominent contemporary authors and texts on the topic include the following: Peter D. Feaver, Guarding the Guardians: Civilian Control of Nuclear Weapons in the United States (Ithaca: Cornell University Press, 1992); Peter D. Feaver, “Command and Control in Emerging Nuclear Nations,” International Security, Vol.17, No. 3 (Winter 1992/93), pp. 160-187; Scott D. Sagan, The Limits of Safety: Organizations, Accidents, and Nuclear Weapons (Princeton: Princeton University Press, 1993); Peter R. Lavoy, Scott D. Sagan, and James J. Wirtz, eds., Planning the Unthinkable (Ithaca and London: Cornell University Press, 2000); Colin S. Gray, National Security and National Style (Lanham, MD: Hamilton Press, 1986); Ashton B. Carter, John D. Steinbruner, and Charles A Zraket eds., Managing Nuclear Operations (Washington, DC: The Brookings Institute, 1987); Paul Bracken, The Command and Control of Nuclear Forces (New Haven, CT: Yale University Press, 1983); and Scott D. Sagan, Moving Targets: Nuclear Strategy and National Security (Princeton: Princeton University Press, 1989).
[7] Feaver, Guarding the Guardians.
[8] Feaver, “Command and Control in Emerging Nuclear Nations,” p. 178.
[9] Feaver, Guarding the Guardians, p. 73; Bruce G. Blair, Strategic Command and Control: Redefining the Nuclear Threat (Washington, DC: The Brookings Institute).
[10] Feaver, Guarding the Guardians, p. 80; Feaver, “Command and Control in Emerging Nuclear Nations,” p. 174, footnote 28.
[11] Peter Stein and Peter Feaver, Assuring Control of Nuclear Weapons: The Evolution of Permissive Action Links (Lanham, MD: University Press of America, 1987), and Scott D. Sagan, Moving Targets.
[12] Strictly speaking, NC3 is not possible or necessary in the case of a lone actor, since with a single actor functioning as both leader and operative, there is no need for the projection of authority at a distance that is the essence of C3.
[13] William Potter and Gary Ackerman, “Catastrophic Nuclear Terrorism: A Preventable Peril,” in Global Catastrophic Risks, Nick Bostrom and Milan M. Circkovic (eds.), Oxford: Oxford University Press (2008).
[14] Gary A. Ackerman and Markus K. Binder, “Pick Your POICN: Introducing the Profiles of Incidents involving CBRN and Non-State Actors (POICN) Database.” Studies in Conflict and Terrorism (forthcoming).
[15] Gary A. Ackerman, Charles P. Blair, Jeffrey M. Bale, Victor Asal and R. Karl Rethemeyer, Anatomizing Radiological and Nuclear Non-State Adversaries, Task 1: Identifying the Adversary. Final Report (College Park, MD, National Consortium for the Study of Terrorism and Responses to Terrorism, 2009).
[16] For purposes of this paper, I define jihadism as Islamists who believe that waging armed struggle against unbelievers (jihad bi-al-sayf, i.e., “jihad of the sword”) is the only path to victory over the forces of “unbelief.” By “Islamism” I refer to a radically anti-Western Islamic political ideology with both revolutionary and restorationist elements. The author thanks Jeffrey Bale for his succinct formulation of these complex topics during personal discussions. See Jeffrey M. Bale, “Islamism and Totalitarianism,” Totalitarian Movements and Political Religions 10:2 (June 2009), esp. pp. 79-80 and 92, note 32. See also, Gary Ackerman and Jeremy Tamsett, “Introduction” in Gary Ackerman and Jeremy Tamsett (eds.), Jihadists and Weapons of Mass Destruction (Boca Raton, FL: CRC Press, 2009), p. xv.
[17] See the list compiled by Erin McNerney, “Appendix B: Selected Jihadist Statements and Discussion on WMD,” In Ackerman and Tamsett (eds.). In addition to Osama Bin Laden’s 1998 justification for pursuit of nuclear weapons, perhaps the most expansive of these is that of Shaikh Nasir bin Hamid al-Fahd, entitled A Treatise on the Legal Status of Using Weapons of Mass Destruction Against Infidels.
[18] See, for example, the 2015 claim in Islamic State’s periodical Dabiq that Islamic State operatives could obtain a nuclear weapon and smuggle it into the United States, “The Perfect Storm.” Dabiq, No. 11. October-November 2015. p. 77. http://jihadology.net/2015/05/21/al-ḥayat-media-center-presents-a-new-issue-of-the-islamic-states-magazine-dabiq-9/.
[19] For a discussion of these attempts, see Ackerman, et. al., Anatomizing Radiological and Nuclear Non-State Adversaries, pp. 75-76; Charles P. Blair, “Jihadists and Nuclear Weapons.” in Ackerman and Tamsett (eds.), p. 214; and Erin McNerney and Matthew Rhodes, “Al-Qa‘ida’s WMD Activities” in Ackerman and Tamsett (eds.).
[20] Patrick Malone, “A terrorist group’s plot to create a radioactive dirty bomb,” Center for Public Integrity (February 29, 2016), accessed from https://www.publicintegrity.org/2016/02/29/19376/terrorist-group-s-plot-create-radioactive-dirty-bomb; Umberto Bacchi, “Belgium demands investigation into possible ISIS infiltration at nuclear power plants,” International Business Times (April 1, 2016), accessed from http://www.ibtimes.co.uk/belgium-demands-investigation-into-possible-isis-infiltration-nuclear-power-plants-1552763.
[21]Andrea A. Nehorayoff, Benjamin Ash, and Daniel S. Smith, “Aum Shinrikyo’s Nuclear and Chemical Weapons Development Efforts,” Gary A. Ackerman (ed.), Designing Danger: Complex Engineering by Violent Non-State Actors: Special Issue of the Journal of Strategic Security, Volume 9, Issue 1 (Spring 2016); Sara Daly, John Parachini, and William Rosenau, Aum Shinrikyo, Al Qaeda, and the Kinshasa Reactor (Santa Monica: RAND Corporation, 2005), accessed at: http://www.rand.org/content/dam/rand/pubs/documented_briefings/2005/RAND_DB458.pdf.
[22] Andrew MacDonald (aka William Pierce), The Turner Diaries ([Place of Publication Not Listed]: National Vanguard Books, 1978), downloaded from http://www.jrbooksonline.com/PDF_Books/TurnerDiaries.pdf on 19 November 2012.
[23] A. C. Thompson, Ali Winston, and Jay Hanrahan, “Inside Atomwaffen as it celebrates a member for allegedly killing a gay Jewish college student,” ProPublica (February 23, 2018), accessed from https://www.propublica.org/article/atomwaffen-division-inside-white-hate-group; “Atomwaffen Division,” Southern Poverty Law Center, accessed from https://www.splcenter.org/fighting-hate/extremist-files/group/atomwaffen-division.
[24] Ackerman, et. al., Anatomizing Radiological and Nuclear Non-State Adversaries and James Halverson and Gary Ackerman, Materials Out of Regulatory Control Threat Assessment (College Park, MD: START, 2017).
[25] Ackerman and Halverson, Materials Out of Regulatory Control Threat Assessment and Phil Williams, Peter Reuter, Richard Arthur, William Cliff, and Gary Ackerman, The Potential Nexus Between Organized Criminals, Terrorists and Radiological Nuclear Smuggling: A Conceptual Discussion (College Park, MD: START, 2012).
[26] Michelle Jacome Jaramillo, “The Revolutionary Armed Forces of Colombia (FARC) and the Development of Narco-Submarines,” in Gary A. Ackerman (ed.), Designing Danger: Complex Engineering by Violent Non-State Actors: Special Issue of the Journal of Strategic Security, Volume 9, Issue 1 (Spring 2016); Gary A. Ackerman, “The Provisional Irish Republican Army and the Development of Mortars,” in Gary A. Ackerman (ed.), Designing Danger: Complex Engineering by Violent Non-State Actors: Special Issue of the Journal of Strategic Security, Volume 9, Issue 1 (Spring 2016).
[27] John Ismay, Thomas Gibbons-Neff, and C.J. Chivers, “How ISIS Produced Its Cruel Arsenal on an Industrial Scale,” The New York Times (December 11, 2017); “Standardisation and Quality Control in Islamic State’s Military Production,” Conflict Armament Research. December 1, 2016, accessed from: http://www.conflictarm.com/publications/.
[28] Columb Strack, “The Evolution of the Islamic State’s Chemical Weapons Efforts,” CTC Sentinel, Volume 10, Number 9. October 2017.
[29] Gary Ackerman, Cory Davenport, Varun Piplani and James Halverson. Trend Analysis of the RN Materials Out of Regulatory Control (MORC) Database. Final Report to NSDD (College Park, MD: START, 2017), p.14. The MORC Database also records almost 200 cases of lower threat nuclear material (uranium enriched to less than 10% U-235) falling out of regulatory control.
[30] Gary Ackerman and James Halverson, “Attacking Nuclear Facilities: Hype or Genuine Threat?,” in Brecht Volders and Tom Sauer (eds.), Nuclear Terrorism: Countering the Threat (New York: Routledge, 2016).
[31] A. Rabasa, et. al., The Lessons of Mumbai (Santa Monica: RAND Corporation, 2009).
[32] James Halverson, “Los Zetas and Proprietary Radio Network Development,” in Gary A. Ackerman (ed.), Designing Danger: Complex Engineering by Violent Non-State Actors: Special Issue of the Journal of Strategic Security, Volume 9, Issue 1 (Spring 2016): 70-83.
[33] “Narcosubmarinos,” Discovery Channel, 2010, available at: http://www.dailymotion.com/video/xw6h6n_discoverychannel-narcosubmarinos_tech. For more details about FARC submarines, see Michelle Jacome Jaramillo, “The Revolutionary Armed Forces of Colombia (FARC) and the Development of Narco-Submarines.”
[34] Charles Blair, “Selected VNSA Incidents and Command and Control,” in Charles P. Blair and Gary A. Ackerman, Terrorist Nuclear Command and Control (College Park, MD: START, 2012). The eight cases assessed were: (a) the Palace of Justice Siege (1985) by M-19 in Colombia; (b) Red Army Faction abductions of 1977 in Germany; (c) the assassination of the Spanish Prime Minister by ETA in 1973; (d) the 2002 Moscow theater takeover by Chechen extremists; (e) the 1995 Chechen Budyonnovsk Hospital hostage crisis; (f) the assassination of former Italian Prime Minister Aldo Moro by the Red Brigades in 1978; (g) the 2008 Mumbai attacks; and (h) the assault on Pakistan Army’s General Headquarters in Rawalpindi in 2009 by the Pakistani Taliban.
[35] Charles Blair, “Selected VNSA Incidents and Command and Control.”
[36] For details on the prospects of such reactors, see S. Khan, et. al., “Nuclear Energy Powered Seawater Desalination,” in Veera Gnaneswar Gude (ed.), Renewable Energy Powered Desalination Handbook: Applications and Thermodynamics (Oxford, UK: Butterworth-Heinemann, 2018).
[37] Fergal O’Brien, “Trump’s Trade War and the $470 Billion Hit to the Global Economy,” Bloomberg (March 12, 2018), accessed at https://www.bloomberg.com/news/articles/2018-03-12/trump-s-trade-war-and-the-470-billion-hit-to-the-global-economy; also see U.S. National Intelligence Council, Global Trends: Paradox of Progress (Office of the Director of National Intelligence, 2017), accessed from https://www.dni.gov/files/documents/nic/GT-Full-Report.pdf.
[38] Gary A. Ackerman and James Halverson, Research Support for Net Assessments: Insight Compendium (College Park, MD: START, November 2016).
[39] For the latter, see Joe Quirk and Patri Friedman, Seasteading: How Floating Nations Will Restore the Environment, Enrich the Poor, Cure the Sick, and Liberate Humanity from Politicians (New York: Free Press, 2017).
[40] Charles P. Blair and Gary A. Ackerman, Terrorist Nuclear Command and Control (College Park, MD: National Consortium for the Study of Terrorism and Responses to Terrorism, 2012).
[41] The experts’ and the model’s estimates concurred completely in three of the six applications, were similar in two of the cases and only differed in a single case. It should be noted, however, that since there is no “ground truth” to empirically validate the model, discrepancies between the experts’ estimates and those of the model do not necessarily imply that the model is inaccurate – it might be the case that the model is outperforming the expert. Blair and Ackerman, Terrorist Nuclear Command and Control, p. 127, footnote 359.
[42] Factor scoring, combination and weighting is more complicated than described here, but this simplified version illustrates the overall operation of the model.
[43] Technically speaking, quantum cryptography does not so much prevent eavesdropping, so much as make it clear to the receiving party that eavesdropping has occurred.
IV. NAUTILUS INVITES YOUR RESPONSE
The Nautilus Asia Peace and Security Network invites your responses to this report. Please send responses to: nautilus@nautilus.org. Responses will be considered for redistribution to the network only if they include the author’s name, affiliation, and explicit consent.


